For long, Apple has held to a notion that somehow, PCs are very susceptible to hacks and viruses whereas Mac is nearly fully secure and that Mac users need not be troubled regarding the security of their machines. However, this seems to be changing now. Apple has taken a clear departure from this former strategy and now seems to be admitting that Mac malware also exist and are a significant threat.
This is quite manifest in the new description that Apple has furnished at its ‘Why You’ll love a Mac’ web page. The older description read:
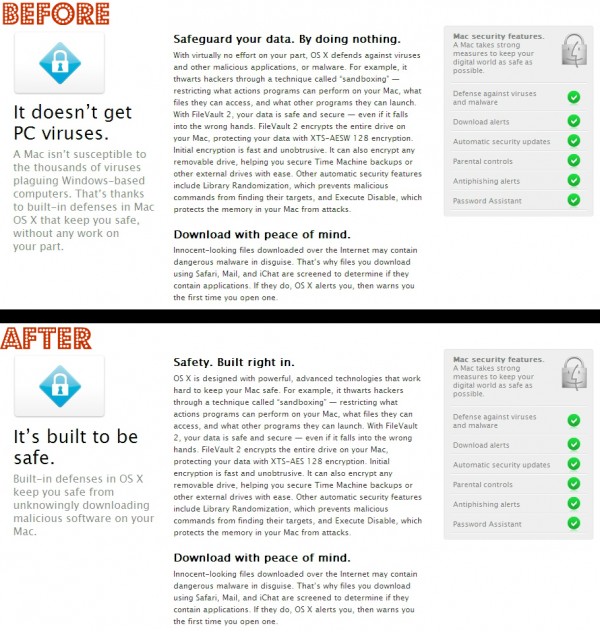
“It doesn’t get PC viruses.
A Mac isn’t susceptible to the thousands of viruses plaguing Windows-based computers. That’s thanks to built-in defenses in Mac OS X that keep you safe, without any work on your part.
Safeguard your data. By doing nothing.
With virtually no effort on your part, OS X defends against viruses and other malicious applications, or malware. For example, it thwarts hackers through a technique called “sandboxing” — restricting what actions programs can perform on your Mac, what files they can access, and what other programs they can launch.”
However, it seems that with increasingly greater knowledge of security online as well as to the users, Apple has realized that it can no longer pitch OS X as a fool-proof software and must admit that Mac OS users also need to be constantly vigilant when it comes to the security of their machines. The new description from Apple reads:
“It’s built to be safe.
Built-in defenses in OS X keep you safe from unknowingly downloading malicious software on your Mac.
Safety. Built right in.
OS X is designed with powerful, advanced technologies that work hard to keep your Mac safe. For example, it thwarts hackers through a technique called “sandboxing” — restricting what actions programs can perform on your Mac, what files they can access, and what other programs they can launch.”
Source: Apple
Courtesy: Giga Om
[ttjad keyword=”mac”]