Universal Plug n Play networking protocols are often used by organizations to allow devices to connect with each other within a network. However, a new research paper reveals, these protocols are highly insecure and can be used by hackers to exploit the millions of devices that make use of UPnP.
UPnP networking protocols are used worldwide in a whole range of devices, including routers and other networking equipment. They are often deployed by organizations because it is easier to use them and the networking costs are significantly trimmed.
However, this convenience may come at a heavy price because UPnP has some serious security flaws. The UPnP discovery protocol, namely SSDP, can be used by a hacker to execute nefarious code as well as gain access to the UPnP control interface, even on a private network. To top things up, certain UPnP protocols provide access to such device functions which are not even mandated as per security regulations.
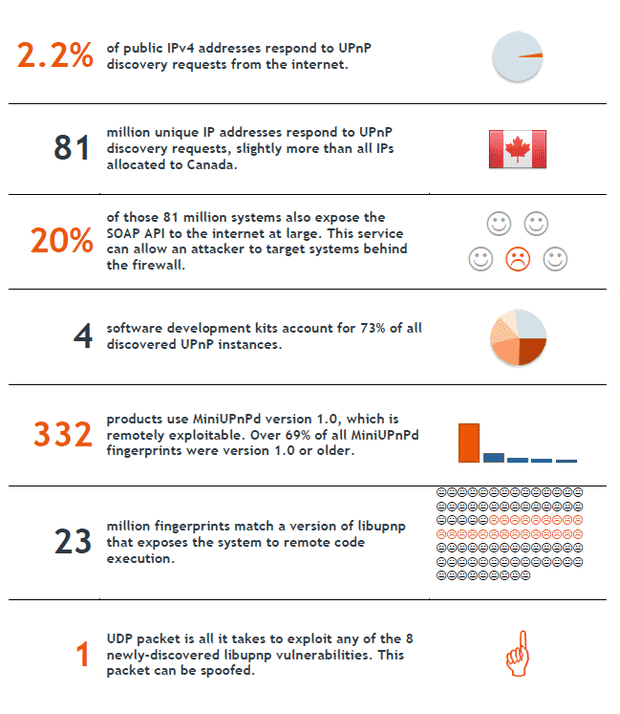
The worst part is that nearly 80 million devices making use of UPnP protocols can be discovered via internet. This gives a potential hacker a huge repository of at-risk devices, which he can then exploit at his leisure.
According to the paper, “In most cases, network equipment that is “no longer shipping” will not be updated at all, exposing these users to remote compromise until UPnP is disabled or the product is swapped for something new. The flaws identified in the MiniUPnP software were fixed over two years ago, yet over 330 products are still using older versions.”
The discovery is certainly frightening in its sheer scope and gives food for thought to organizations who tend to take the security of their internal networks lightly.
Source: Security Flaws in Universal Plug and Play: Unplug, Don’t Play
Courtesy: CNET
[ttjad keyword=”wireless-router”]