Adding PIN lock to your mobile handset may give you a sense of security; having your data encrypted may make you think that even if you lose your handset, your data would be safe. But in all, both of them may prove inadequate in the face of a ‘frost attack’ which literally uses cold temperatures to bypass these security measures.
The attack is known as the ‘cold boot attack‘ and it fundamentally rests on the principle that when a phone is cooled, the retention of its memory increases. This gives the prospective hacker sufficient time to read whatever the temporary memory holds before it is erased.
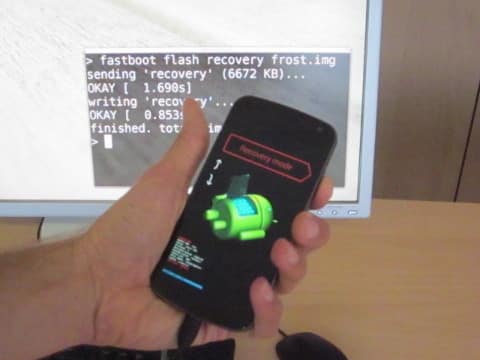
Researchers at Erlangen University in Germany have now demonstrated that such an attack can be used to easily bypass the PIN security. In fact, the attack may even be used to access the encryption key of the device and thus, read the encrypted data on an Android handset. They have aptly named their technique FROST, which stands for ‘Forensic Recovery of Scrambled Telephones.’
Tilo Mueller and Michael Spreitzenbarth demonstrated the attack by cooling down a Samsung Galaxy Nexus to five degrees Fahrenheit and then quickly rebooting it. The process allowed them to read emails, web browsing details, images as well as the encryption key in some cases.
Explaining the concept behind this attack, Mueller explains, “RAM doesn’t lose its content immediately. If it’s 30 degrees Celsius it’s lost in one or two seconds. But if you cool the phone, the contents are lost in five or six seconds. That gives us enough time to reboot the phone and access the memory.”
In the quick reboot while the RAM retains information for a few seconds, you can plug in a USB and copy the data. While carrying out the attack on an Android handset was fairly easy, the researchers feel that pulling a similar trick on an iOS device may be harder.
Source: Informatik
Courtesy: Forbes