Apple’s iPhone is considered as one of the most secure devices, given the fact that Apple’s iOS comes with fairly tight security measures. However, now and then, we caught a glimpse of a flaw or a loophole even in such security. Recently, there were reports about successful SMS spoofing attacks against iPhone. Now, Apple has responded to these reports.
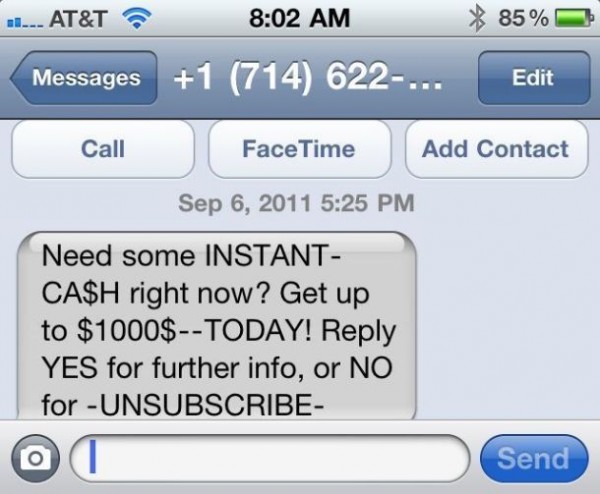
Basically, SMS spoofing works like this. You receive a message from an individual and that individual can specify any number other than his own to receive your reply. So when you respond to such a message, your message essentially goes to some other number than the one which sent you the message.
The tech news were abuzz recently when it was revealed that even iPhone was vulnerable to such an attack. Now, Apple has chosen to respond to this news.
According to Apple, “Apple takes security very seriously. When using iMessage instead of SMS, addresses are verified which protects against these kinds of spoofing attacks. One of the limitations of SMS is that it allows messages to be sent with spoofed addresses to any phone, so we urge customers to be extremely careful if they’re directed to an unknown website or address over SMS.”
As it turns out, SMS spoofing attack can be launched against virtually any mobile platform and there is no effective way to thwart it. There are many services which offer the ability to appear anyone else when sending a text message. Naturally, this does pose a certain security risk to the user who receives such a text. But then, one should always be careful in texting and shouldn’t reveal any sensitive information.
Source: Engadget
[ttjad keyword=”hot”]

Apple’s iPhone is considered as one of the most secure devices, given
the fact that Apple’s iOS comes with fairly tight security measures.
However, now and then, we caught a glimpse of a flaw or a loophole even
in such security.
http://incentiveproperties.com/