Mobile devices run a very high risk of being stolen, due to their size and the sheer ease with which they can be stolen. Apple has been trying to effectively counter the dislocation of its devices, helping customer recover them. Now, a new Apple patent application indicates that Apple may be working on a some more advanced tools to this end.
The patent application titled ‘Proactive Security for Mobile Devices’ has been credited to Apple engineer Hooman Borghei. According to this application, a number of new security methods have been explored that may be used in case of such mobile devices which are stolen or lost.
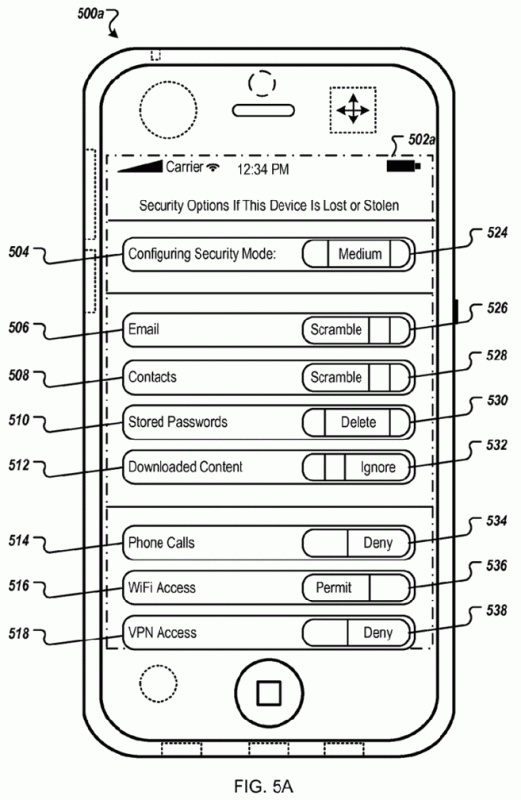
For instance, if a culprit enters the wrong passcode on a user’s lost mobile device, a certain mechanism comes into effect which selectively protects the data on the device. Moreover, a number of remote surveillance capabilities are also being discussed.
For instance, the application talks about transmitting the images and sounds from your device secretly after it is being stolen. This may help identify the culprit who stole the device.
According to the application, “A mobile device can proactively determine whether the mobile device is associated with a security risk and the level of the security risk. Upon determining a security risk, the mobile device can transmit coordinates of its current geographic location to a server.”
In a way, Apple is probably attempting to make the security mechanism of a stolen device more ‘intelligent’ to make it realize that it is no longer in the hands of its rightful owner. The application further states, “If multiple failed password attempts are detected, the mobile device can proactively increase a security level of the device, and selectively protect files or other content stored on the mobile device. In some implementations, the mobile device can be transitioned into a surveillance mode where the mobile device records or captures information associated with one or more of user actions, ambient sound, images, a trajectory of the device, and transmits the recorded or captured information to the network resource.”
Maybe they will use this in “Find My iPhone” application in future.
Source: USPTO
Courtesy: 9to5mac

![Read more about the article Jailbreak iOS 4.3 on iPhone, iPad and iPod touch With Pwnage Tool Bundle[How To]](https://thetechjournal.com/wp-content/uploads/2011/01/Jailbreak-iPod-touch-4G-on-iOS-4.3-200x300.jpg)
