Digital security is becoming an increasingly greater problem with billions of users hooked to the internet now. Every other day, we hear of some serious sort of security loophole which ends up compromising the data of individuals and organizations. This now, for instance, it was a writer for Wires, Mat Honan, who was a victim of a cyber attack from hackers.
The attack ended up causing a lot of damage to Honan. The hackers first fooled Apple representatives and into believing they were the actual users and then had them reset the password on Honan’s iCloud. Once this was done, they were then able to access all linked social media accounts. This included not only Honan’s accounts but also Gizmodo’s Twitter account.
This, and other similar instances like this, makes it appear that breaking into one’s account and stealing one’s data is becoming increasingly easy for the hackers. But some very interesting suggestions are floating on the web as to how to ramp up digital security.
One basic suggestion is to couple actual digital security, for instance passwords etc, with biometric security. This can be done by adding the requirement of gathering, say, finger prints of the user every time he wishes to log in. But that of course requires special hardware and may also prove cumbersome for the users.
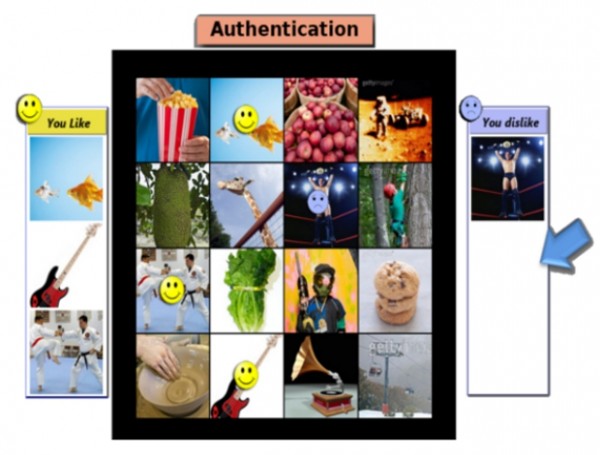
Another way to accomplish better security is, as suggested by Dr. Jakobsson, to make use of ‘Visual Preferences.’ Other touted names for the technique are ‘Mental metrics.’ The basis of this technique is that when given a mixture of pictures, a person would like some of them and dislike others, based on his mental facilities and experiences.
These picture preferences can be recorded by the system and user can later be asked about them to confirm his being. According to Dr. Jakobsson, not anyone apart from a person’s family may be able to guess precisely at these preferences and even they can’t deduce it exactly.
This may sound new and extra-ordinary but the fact is that it is already being used in a number of companies. And many others firms have plans of implementing this soon. So it is perhaps high time that social media sites such as Facebook and Twitter also jumped this bandwagon to improve the security of their users.
Source: ZDNet
[ttjad keyword=”keyboard-mouse”]