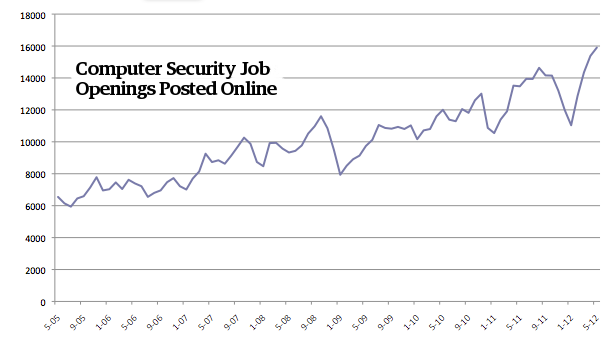
Earlier today, I wrote about Mikko Hypponen’s, chief research officer of F-Secure, hypothesis of government spies infiltrating Microsoft. But he has something more to say. Lately, Mr. Hypponen has spent a lot of time looking at job openings of US defense contractors’ websites and online job listings to find out actual candidates with secret clearances who has been searched job to use specific keyword like “exploit”, “offensive”, and “vulnerability”. What he has seen over the last couple of months is pretty interesting. Job posting trends show that the US defense contractors are out for hiring offensive hackers, and they don’t only intend to protect US cyberspace but also intend to exploit the loopholes of cyber security.
Mr. Hypponen has drawn our attention to job descriptions at multiple openings. One job listing for “Cyber Software Engineer” at defense firm Northrop Grumman reads, “this exciting and fast-paced Research and Development project will plan, execute, and assess an Offensive Cyberspace Operation (OCO) mission.” Another firm Booz Allen Hamilton seeks a “Target Digital Network Analyst” capable of “exploit development for personal computer and mobile device operating systems, including Android, Blackberry, iPhone and iPad.”
Defense contractor giant Raytheon is seeking for a “Unix Attack developer.” TeleCommunications Systems wants a “Windows Attack/Exploit Developer.” NSA contractor SAIC seeks a “Red Team Developer.” All three of those companies’ job descriptions include the phrase: “analyzing software for vulnerabilities as well as development of exploit code.”
Hypponen said “I think this is new, the arms race has started, and this proves it. It’s a clear sign of the demand to stockpile cyber weapons and expand the operations underway.” Recent reports also suggests that Hypponen could be right.
Source: Forbes
[ttjad keyword=”best-selling-gadget”]