Wikileaks has long been eyed as something that is dangerous and undesirable by the authorities, especially in US. However, the data divulged by Wikileaks is now being put to a use that may change this opinion in Washington. Researchers are using the leaked data on Wikileakes to predict the rise in insurgency in different Afghan regions.
This has now been reported in Proceedings of the National Academy of Sciences. In the study undertaken by the researchers, 77,000 logs from the Afghan War Diary were analyzed. These logs were released by Wikileaks on July 25, 2010. The logs contain information about the insurgencies that occurred during 2004 and 2009.
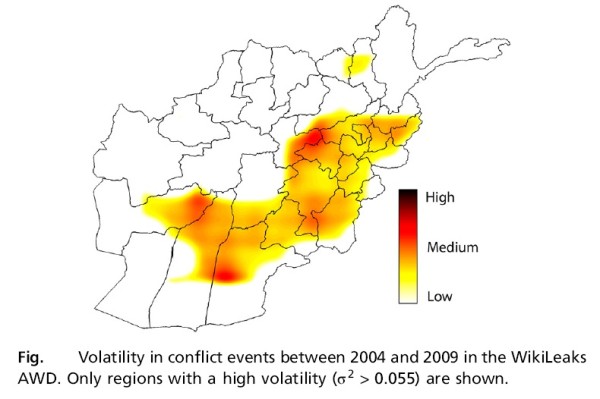
With the help of this huge sample size, researchers have been able to come up with an algorithm that can predict future insurgencies. The algorithm takes into account the ‘volatility’ of a region to accurately predict future insurgencies. If the volatility of a region is high, it becomes hard to accurately predict future incidents. However, if the volatility is low, the algorithm is able to predict future events quite accurately.
For instance, the Baghlan province in Afghanistan is not too volatile. In 2009, 100 insurgent incidents were reported in the province. Based on the algorithm, the researchers predicted that in 2010, this number would rise to 228. The actual number of insurgent events that occurred in 2010 were 222. That is very close to the predicted number, showing how accurate the algorithm is.
But, don’t hold your breath thinking the hawks in Washington will open up towards the whole concept of such data leaks and begin to tolerate them, because of its new found usefulness.
Source: PNAS
Courtesy: The Verge
[ttjad keyword=”xbox-360″]



The volatility is low, the algorithm is able to predict future events quite accurately.
http://www.appster.com.au/