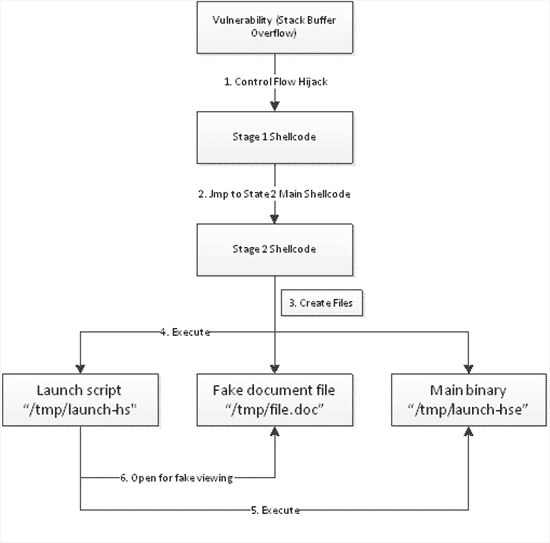
Given the immense expansion of the tech population, it is only inevitable that some security loopholes will go unnoticed for years. Same is the case with a number of exploits in Microsoft’s Office for Mac. Researchers at Microsoft have found out these flaws only now when a new malware attempts to exploit them. The flaws are there in the three-year-old version of Office for Mac.
The flaw is not too easy to exploit and thus, hasn’t been used to infect a lot of machines. It makes use of a multi-stage attack to infect the targeted machine.
According to Microsoft, it did fix the flaw back in 2009. However, a lot of machines haven’t been updated with the fix and so, continue to be vulnerable. The company’s blog states, “No operating system that exists outside a laboratory is entirely immune to malware. “As different operating systems continue to gain in popularity they attract more attention from would-be attackers – especially since, as we see in the example analysis above, the techniques and understanding needed to do so may be much the same as those used against other platforms. And even though an operating system may include many risk-reducing mitigation technologies, any machine’s defenses against vulnerabilities are directly related to how current its security updates for applications are kept.”
The users who are potentially in danger of getting their machines infected because of the exploit includes those who are currently using Office 2004 for Mac, Office 2008 for Mac and Open XML File Format Converter. Microsoft has warned the users of these versions of Office to update their software as soon as possible. The updates can be found on Microsoft’s Security Bulletin here.
Source: Microsoft
Courtesy: BGR
[ttjad keyword=”all-in-one-desktops”]