Last year, the users of Mac were alerted over the security of their systems when a Mac trojan called ‘FlashBack’ was discovered. The trojan posed as a Flash Player Installer. When the trojan was discovered, Apple took steps to alert the users and also counter the threats of trojans by using the File Quarantine system. Now it has been reported that the authors of the malware have tweaked it so that is now adopts a multi-prong strategy to infiltrate the user’s system. This new variant has been termed Flashback.G.
The new variant of the Flashback trojan tries to infiltrate the Mac system of users through multiple strategies. The first two methods deployed by the trojan make use of the Java vulnerabilities. The users who are using the updated versions of Java need not worry about this particular method because this has been patched in recent versions. But the trojan may silently infect such systems which are still using the older versions of Java.
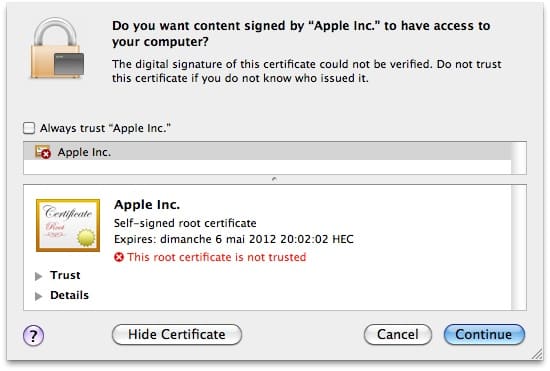
The other method this trojan deploys, in case it can’t make use of Java vulnerabilities, is to then present itself as a self-signed certificate from Apple trying to fool the users so that they may allow it to get installed on their systems. If users give the permission, the trojan installs itself on the system and then starts looking for usernames and passwords stored on the system. According to the analysis of the trojan, “This malware patches web browsers and network applications essentially to search for user names and passwords. It looks for a number of domains – websites such as Google, Yahoo!, CNN; bank websites; PayPal; and many others. Presumably, the people behind this malware are looking for both user names and passwords that they can immediately exploit – such as for a bank website – as well as others that may be reused on different sites.”
The easy way of fending off the security threat posed by this particular variant of Flashback is simply to keep Java on your Mac up to date and to be aware of the social engineering trick of the trojan in which it may pose to be an Apple-signed software.
[ttjad keyword=”mac”]