We reported earlier that a number of tech analysts around the globe are identifying the recently-discovered Flame malware as the most nefarious malware that has been known to date. The complexity and functionality of Flame is unmatched by any other malware that exists today. Now, security analysts are breaking down Flame to identify which of its modules are the most nefarious.
According to the folks at Secure List, they have been looking for a zero-day exploit in Flame since without it, this malware couldn’t have infiltrated the patched and secured Windows 7 machines. And now, they have found one.
The infection of machines is accomplished through two main modules of Flame. These modules are called ‘Gadget’ and ‘Munch. Both work together and launch a sophisticated man-in-the-middle attack.
This is how it works. The initial Flame infection happens through a zero-day vulnerability. Once a machine within a network is infected with Flame, the Gadget and Munch modules come into effect. When a machine tries to connect to Windows Update, the connection is redirected and moved towards an infected machine. The infected machine, in turn, sends a fake Windows Update to the target machine. The text is as follows:
“update description=”Allows you to display gadgets on your desktop.”
displayName=”Desktop Gadget Platform” name=”WindowsGadgetPlatform”>
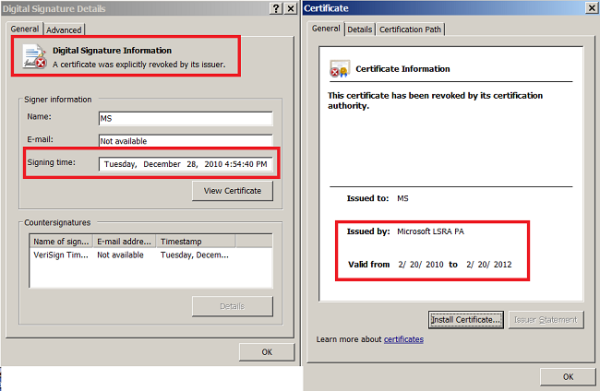
8 CAB file are used in this process to successfully infect a target machine, among them a main program called WuSetupV.exe. It’s a tiny program, sized 28KB, which contains a fake Microsoft signature. The fake signature helps the program to run in the target machine without raising any security flags.
The good thing is that Windows has released updates to block fake certificates used by Flame. Windows users are highly advised to apply these updates as soon as possible.
Source: Secure List
[ttjad keyword=”cloud-storage-drive”]