After the launch of his online storage service, Mega, Kim Dotcom had offered reward to the tune of $13,500 to such users who’d discover security vulnerabilities in the service. As it happens, seven bugs have been reported and fixed so far and three cash rewards have been handed out by the company.
The handouts suggest that Dotcom is indeed serious in making his service impregnable in terms of security. However, the fact that seven bugs were found during the first week alone tends to hint that the service may not be so secure for now.
Dotcom has stated that the reward program is meant for the long-term and as users keep finding newer bugs, they will be rewarded in cash for their discoveries. The seven bugs found during the week and deemed eligible for bounty are listed below:
- One Class IV vulnerability: Invalid application of CBC-MAC as a secure hash to integrity-check active content loaded from the distributed static content cluster. Mitigating factors: No static content servers had been operating in untrusted data centres at that time, thus no elevated exploitability relative to the root servers, apart from a man-in-the-middle risk due to the use of a 1024 bit SSL key on the static content servers. Fixed within hours.
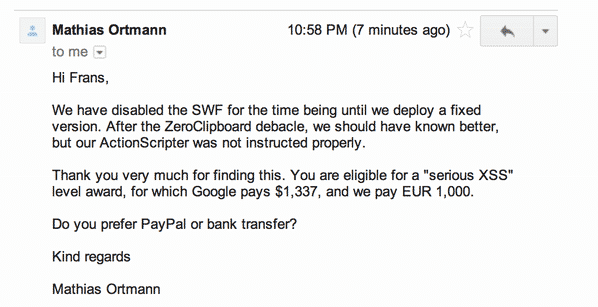
- Three Class III vulnerabilities: i) XSS through file and folder names. Mitigating factors: None. Fixed within hours. Ii) XSS on the file download page. Mitigating factors: Chrome not vulnerable. Fixed within hours. iii) XSS in a third-party component (ZeroClipboard.swf). Mitigating factors: None. Fixed within hours.
- One Class II vulnerability: XSS through strings passed from the API server to the download page (through three different vectors), the account page and the link export functionality. Mitigating factors – apart from the need to control an API server or successfully mounting a man-in-the-middle attack –: None. Fixed within hours.
- Two Class I vulnerabilities: i) HTTP Strict Transport Security header was missing. Fixed. Also, mega.co.nz and *.api.mega.co.nz will be HSTS-preloaded in Chrome. Ii) X-Frame-Options header was missing, causing a clickjacking/UI redressing risk. Fixed.
While we don’t know exactly what amounts of bounties were handed out to those who discovered the bugs, Dotcom did reveal that at least one of the finders was awarded a cash prize of EUR 1000.
Courtesy: TNW
[ttjad keyword=”cloud-storage-drive”]