In many movies, we have seen people easily hacking traffic signal system and then controlling it. But in reality is it possible to hack traffic signal system easily? Well, security scientists at the University of Michigan have mentioned that in real life, it’s really possible that anyone can hack traffic signal system just by using a laptop and the right sort of radio.
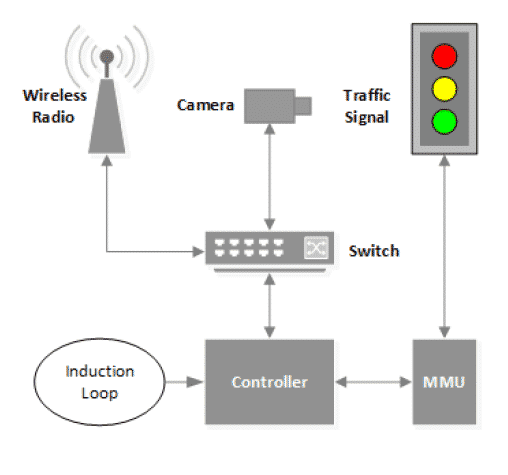
The traffic lights use a combination of 5.8 GHz and 900 MHz radio signals, contingent upon the conditions at every intersection, for wireless correspondence in point-to-point or point-to-multipoint designs. The 900 MHz connections utilize “an exclusive convention with recurrence bouncing spread-spectrum (FHSS),” yet the 5.8 GHz version of the proprietary protocol is not quite the same as 802.11n. However, security scientists at the University of Michigan wanted to see is it really possible to hack traffic signal system so easily the way it is shown in movies like Die Hard and The Italian Job?
Well to find the answer, they did an experiment. During the experiment, scientists discovered some loops and holes in traffic signals. The scientists said that the network traffic frameworks are left helpless against three real vulnerabilities:
- Decoded radio signs.
- Utilization of factory set usernames and passwords.
- A debugging port that is not difficult to attack.
According to the scientists, these things leave the network accessible to everyone from professional hackers to script kitties. However, using a laptop and a radio, the scientists hacked the traffic signal system and later asserted that it’s really “shockingly simple” for anybody to hack traffic signal system with a laptop and a radio.
Researchers also said that anybody with a laptop and a wireless card working on the same frequency as the wireless network traffic light — for this situation, 5.8 gigahertz — could get to the whole decoded system of networks.
In a paper study, the security researchers have mentioned that how an arrangement of real security vulnerabilities in traffic light frameworks permitted them to effortlessly and immediately seized control of the entire system of no less than 100 traffic signals in Michigan city from a solitary point of access. Specialists took permission from the road agency before performing the test, yet they didn’t reveal precisely where in Michigan did they perform these exciting tests.
Source: The Hacker News
[ttjad keyword=”security”]




culinary arts school in virginia [url=https://otvetnow.ru]https://otvetnow.ru[/url] payroll accounting basics