Traditionally, Microsoft’s operating system as well as software have been considered as fraught with vulnerabilities. That was true until a few years ago. But now, the latest list of top 10 vulnerabilities released by Kaspersky prove that Microsoft has come a long way since.
The list by Kaspersky cites the top 10 vulnerabilities that were exploited by hackers during the third quarter. Not very surprisingly, the list is topped by a number of Java vulnerabilities. In the recent past, we have seen a number of Java vulnerabilities surface, putting millions of users at the danger of having their machines compromised.
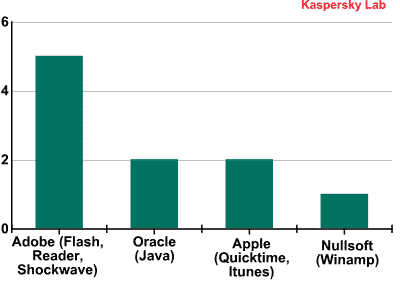
Next on the list are a few Adobe Flash Player and Adobe Reader vulnerabilities. These vulnerabilities have been deemed as highly critical by the anti-virus company which means that they are a huge security risk for the end users.
What is intriguing is that although Microsoft is nowhere to be seen on the list, Apple has been included. Its QuickTime and iTunes software have multiple vulnerabilities, according to Kaspersky. And by making use of these highly critical vulnerabilities, a hacker can gain local user privileges on a hacked system.
Top ten vulnerabilities:
The briefly detailed list of the top ten vulnerabilities found by Kaspersky is as follows:
- Oracle Java Multiple Vulnerabilities: DoS-attack (Gain access to a system and execute arbitrary code with local user privileges) and Cross-Site Scripting (Gain access to sensitive data). Highly Critical. It was detected on the computers of 35% users.
- Oracle Java Three Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Extremely Critical. Detected on the computers of 21.7% users.
- Adobe Flash Player Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Gain access to sensitive data. Highly Critical. Found to be on the computers of 19% users.
- Adobe Flash Player Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Bypass security systems. Highly Critical. Found to be infecting 18.8% of the users.
- Adobe Reader/Acrobat Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Extremely Critical. Detected on 14.7% computers.
- Apple QuickTime Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Highly Critical. Found on 13.8% computers.
- Apple iTunes Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Highly Critical. Detected on 11.7% computers.
- Winamp AVI / IT File Processing Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Highly Critical. Detected on 10.9% computers.
- Adobe Shockwave Player Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Highly Critical and infecting 10.8% computers.
- Adobe Flash Player Multiple Vulnerabilities: Gain access to a system and execute arbitrary code with local user privileges. Bypass security systems. Gain access to sensitive data. Extremely Critical. Found on 9.7% computers.
Kaspersky also revealed general statistics to go with the list. For instance, according to the company, “56 percent of exploits blocked in Q3 use Java vulnerabilities.” In other words, a majority of digital security problems for common consumers were a direct result of Java’s flawed security.
Microsoft, on the other hand, deserves a commendation for having achieved the mighty feat. Only a few years ago, the company’s products were considered security risks and liabilities. Now, with the journey up to Windows 8, Microsoft has been able to turn its operating system as well as other software into fairly secure products.
Source: Kaspersky Labs
Courtesy: TNW
[ttjad keyword=”windows-tablet”]