DDoS attacks are a routine thing for the entities plugged into the internet. However, a recent attack made some clever use of a video site’s exploit to launch a DDoS attack. It used 22,000 unwitting site visitors to DDoS the target.
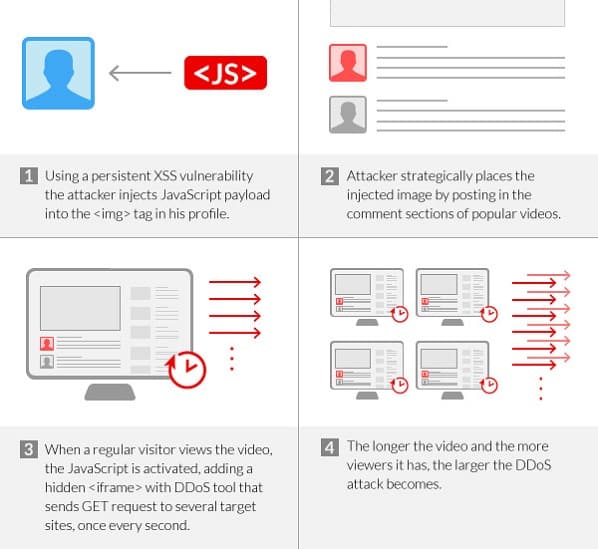
According to the security firm Incapsula, the site in question is one of the most popular video sites and the exploit was a web application vulnerability. The attackers who masterminded it all created a malicious JavaScript which was then embedded inside the image icons used for accounts.
As soon as a person viewed any post by the compromised user, the attack code would be launched and his account would then be used to send out one request per second to the target machine. In total, the malicious JavaScript was able to reach out to 22,000 user accounts, prompting a barrage of millions of requests per second to the target.
The malicious JavaScript essentially made use of a cross-site scripting vulnerability in the site. Such a vulnerability allows an attacker to insert malicious JavaScript code on the vulnerable site. The code executes every time a user visits the compromised page where the said JavaScript is installed.
Commenting on this clever DDoS attack, Ronen Atias and Ofer Gayer of Incapsula stated, “Obviously one request per second is not a lot. However, when dealing with video content of 10, 20, and 30 minutes in length, and with thousands of views every minute, the attack can quickly become very large and extremely dangerous. Knowing this, the offender strategically posted comments on popular videos, effectively created a self-sustaining botnet comprising tens of thousands of hijacked browsers, operated by unsuspecting human visitors who were only there to watch a few funny cat videos.”
Source: Incapsula
[ttjad keyword=”atnt-contract-phone”]