Microsoft had to face a very embarrassing situation when it was discovered that a proof-of-concept code which can be a very serious security threat for Windows, was actually leaked from the Microsoft Active Protection Program (MAPP). This malicious code lets the developers discern the possible exploits in Microsoft’s implementation of RDP protocol and then use these exploits for nefarious purposes.
One of the many possible exploits that could be launched using this proof-of-concept code is to launch DoS attacks against unpatched Windows systems. According to one of the director of Microsoft’s Trustworthy Computing Group, “We continue to watch the threat landscape and we are not aware of public proof-of-concept code that results in remote code execution.”
What is appreciable is that Microsoft was quick to furnish a patch to look to this security loophole. The MS12-020 patch updates the system to protect it against possible CVE-2012-0002 exploits.
So far, it hasn’t been found out exactly where the leak came from. The MAPP partners are bound not to divulge any Microsoft-related information under a ‘strict Non-Disclosure Agreement.’
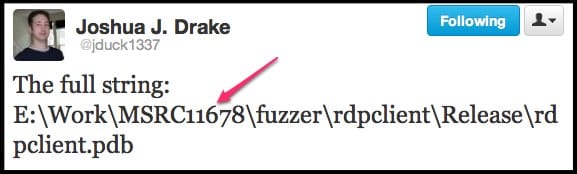
So how was it found out that the actual leak came from Microsoft? It was basically an intelligent analysis of a string that was found in the proof-of-concept code. The string contains the term ‘MSRC11678’ which refers to Microsoft Security Response Center number assigned to this particular vulnerability. A number of analysts have criticized Microsoft for not timely handling the security problem even when it was well aware of it.
You can access the security patch from Microsoft to address the vulnerability over here.
[ttjad]