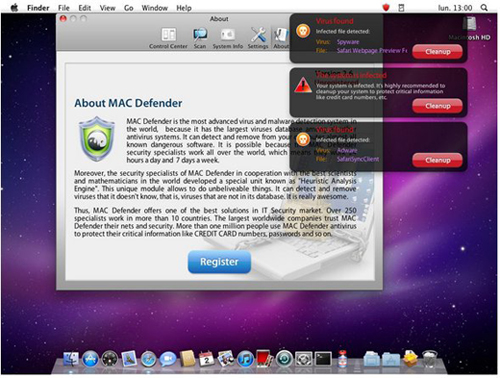
Apple’s Mac is vulnerable, as shown by a variant of the MAC Defender malware that doesn’t require an administrator’s OK to install and the irst version did require the administrator’s password before stealing credit-card information, but new MAC Defender variant, called MacGuard, bypasses security by installing in a new location…….
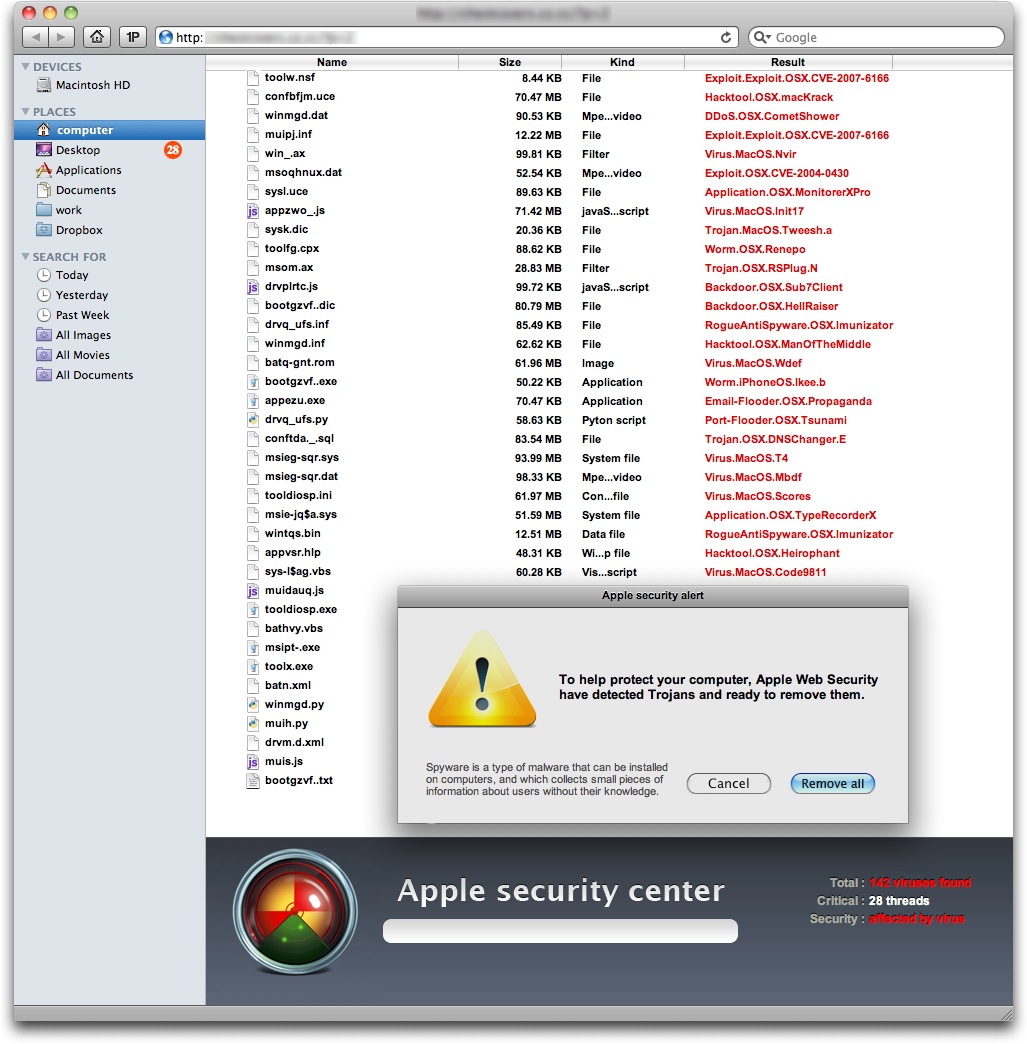
There’s a newer version of the MacDefender scareware program that’s now showing up on various Web sites and this one no longer requires a user to enter her administrator password during the installation process in order to complete the infection routine. It comes in two parts: the irst part is a downloader, a tool that, after installation, downloads a payload from a web server. As with the Mac Defender malware variants, this installation package, called avSetup.pkg, is downloaded automatically when a user visits a specially crafted web site. If Safari’s “Open ‘safe’ files after downloading” option is checked, the package will open Apple’s Installer, and the user will see a standard installation screen. If not, users may see the downloaded ZIP archive and double-click it out of curiosity, not remembering what they downloaded, then double-click the installation package. In either case, the Mac OS X Installer will launch. Unlike the previous variants of this fake antivirus,no administrator’s password is required to install this program. Since any user with an administrator’s account – the default if there is just one user on a Mac – can install software in the Applications folder, a password is not needed. This package installs an application – the downloader – named avRunner, which then launches automatically. At the same time, the installation package deletes itself from the user’s Mac, so no traces of the original installer are left behind.
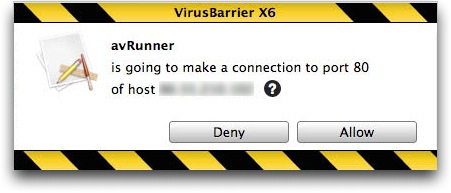
The second part of the malware is a new version of the MacDefender application called MacGuard. This is downloaded by the avRunner application from an IP address that is hidden in an image file in the avRunner application’s Resources folder. (The IP address is hidden using a simple form of steganography.) Intego VirusBarrier X6’s Anti-Spyware feature detects this operation:
Intego considers that the risk for this new variant to be medium, in part because the SEO poisoning has been very efficient in leading Mac users to booby-trapped pages, but also because no password is required to install this variant.The first thing to do is make sure that when seeing a web page that looks like a Finder window, and purports to be scanning your Mac, you know that this is bogus. Leave the page, and quit your web browser. If anything has downloaded, and the Installer application has opened, quit it right away; look in your Downloads folder for the file, then delete it. Next, users should uncheck the “Open ‘safe’ files after downloading” option in Safari’s General preferences. Intego VirusBarrier X6 protects users from this malware with malware definitions dated May 25, 2011 or later. VirusBarrier X6’s real-time scanner will detect the file when it is downloaded, and its Web Threats protection blocks web pages containing this malicious code. VirusBarrier Express and VirusBarrier Plus, available exclusively from the Mac App Store, detect this malware with malware definitions dated May 25, 2011 or later, but these programs do not have a real-time scanner, due to limitations imposed by the Mac App Store; users should scan their Macs after they have updated to the latest malware definitions.
Download Intego VirusBarrier X6 : Here
[ttjad keyword=”mac”]

Got… “automatically”…infected with this malware while visiting a site. If you happen to get this rascal…do a Google search…”How To Avoid or Remove… ‘MAC Defender” (Posted by Apple, Article: HT4650 – Dated: May 24, 2011)
variants…’MACProtector’ and ‘MACSecurity’
I Followed the instructions on HT4650 and removed the infected files. Have a fellow MAC user and he has….ClamXav for MAC on his laptop. It’s a free program with donations accepted. I downloaded it and sure enough up came…avsetup.pkg on my hard drive. (This is the file for Malware: OSX/MACDefender) This great little program – ClamXav – has a Sentry Tab in which you can check to Quarantine and check to Delete. Performed this function and …deleted the avsetup.pkg file on my hard drive. I am in no way connected to ClamXav nor am I promoting it. Use at you own decision.
As a final note…have seen on the web that Apple may release an OSX update to remove this Malware. Certainly hope sooner than later…..Tim?
rusty7vine@gmail.com Minnetonka, Minnesota May 28, 2011