A Russian hacker recently gained a lot of fame and notoriety when it was discovered that he was able to create an exploit which allowed free in-app purchases for iOS users. The hacker’s name is Alexei Borodin. Borodin’s exploits don’t end there. He is back in the news with a new exploit which allows Mac users to perform similar free in-app purchases when using Mac apps.
How is the exploit accomplished?
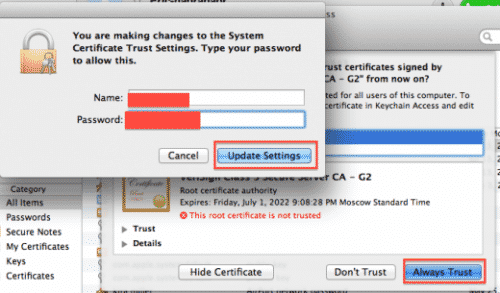
First of all, two local certificates are installed. Next, the user routes the DNS settings of his computer to Borodin’s servers. Borodin’s servers pretend to be the Mac App Store and verify the purchase.
To complete the whole process, users have to run a companion app on their machines. This companion app is called ‘Grim Receiper.’ With the help of the false verification and this companion app, the exploit is able to bypass Apple’s receipt system. According to the hacker, so far about 8,460,017 free purchases have been performed using his exploit.
Apple has recently announced that it will soon patch up the vulnerability with iOS 6. This solution will essentially allow the developers to encrypt and verify their digital receipts with Apple. In-app purchases are very popular among iOS users and thus, the exploit by the Russian hackers will significantly impact iOS ecosystem until Apple patches up the exploit.
That would solve the problem for iOS developers. But now, Apple will need to introduce a similar solution for Mac developers too. Although in-app purchases are not that popular with Mac users, they are still a significant part of the Mac ecosystem.
Courtesy: TNW
[ttjad keyword=”ipad”]