Apple is planning to launch its own social network especially developed for iOS users and the app could help iOS users find other Apple fans who are nearby. If brought to devices in an update of the mobile operating system, which allow users to meet new compatible buddies in their vicinity as handsets communicate wirelessly and this is a ad hoc networking based on content and location. The new patent filing shows that the Cupertino firm could soon be set to offer its own social offering with iPhone, iPad and iPod Touch users all able to meet and communicate with fellow iOS users either at their current location or in regions they have recently visited and not just for existing friendships the patented Apple network will see users remotely paired with other iOS users based on music preferences, video plays, pictures snapped, websites visited and applications they have downloaded………..
A new patent application from Apple reveals that they began working on new security features for “Find My iPhone” shortly after the first iteration was revealed back in 2009. The next generation security features are noted as being proactive in nature. The user will be able to preselect certain files to be protected in the event their device is lost or stolen and introduces ways of securely scrambling information instead of wiping it out to make retrieval easier. Mobile devices, such as phones and media devices, have a high risk of being lost or stolen. If a mobile device is stolen, the information contained on the device could be accessed. Various security methods have been developed to prevent unauthorized access of information stored on mobile devices. Some methods will encrypt the data to prevent access. Simple encryption ciphers could be broken and more secure encryption techniques are also more complex and thus require more resources that may not be available on some devices. Other security methods allow a remote wipe command to be sent to the mobile device over a network. The remote wipe command, however, wipes out all the data on the mobile device accept a boot file. This forces the user to have to restore the wiped data, which could be inconvenient and time consuming for the user.
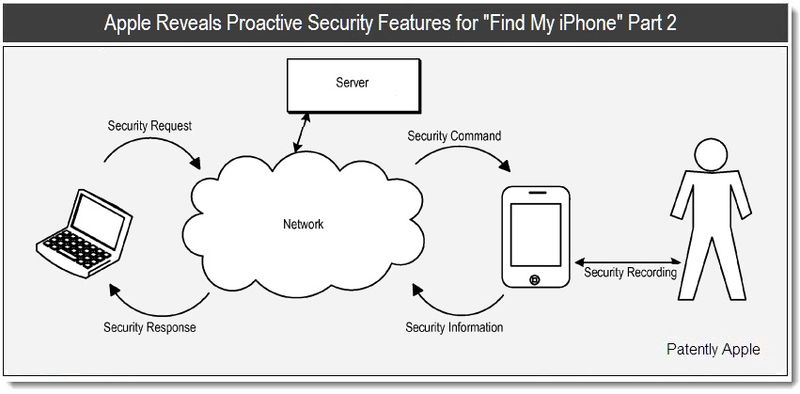
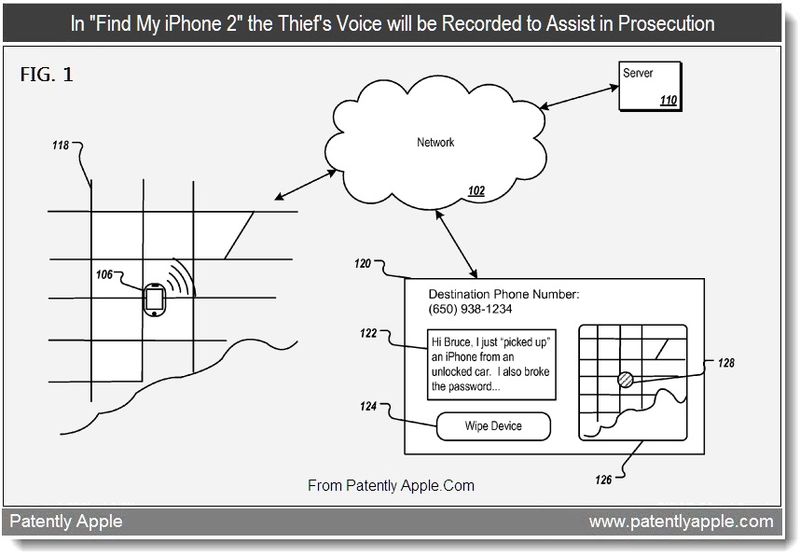
Apple‘s patent application covers methods, program products and systems for proactively securing mobile devices. A mobile device could proactively determine whether the mobile device is associated with a security risk and the level of the security risk. Just as with Find My iPhone , the user could remotely set a passcode lock and block an unauthorized user from activating the phone. What’s new here is that if multiple failed password setting attempts are detected, the mobile device could determine that the device is currently being operated by an unauthorized user, and could proactively increase a security level of the device. Under the increased security level, files or other content stored on the mobile device could be selectively protected. In some implementations, the mobile device could be transitioned into a surveillance mode where the mobile device records or captures information associated with one or more of user actions, ambient sound, images, a trajectory of the device and transmits the recorded or captured information to the network resource.
The user could have granulated protection of data stored on the mobile device. The user could selectively wipe or scramble the data when the mobile device is lost or stolen. Thus, the user could avoid having to wipe the entire device clean when the whereabouts of the device is unknown. When the data are scrambled rather than wiped, if the user subsequently recovers the mobile device, the data can be unscrambled. The user will not face a complete loss of data. Access to function and programs stored on a lost or stolen mobile device could be selectively limited before the device is recovered. For example, functions that could incur costs to the user (e.g., long distance phone calls, text messaging, and data access) can be disabled. Security breach to corporate network could be prevented, for example, by changing the VPN settings upon detection of security risk. Technology for proactively securing a mobile device could protect a user’s privacy by allowing an authorized user to disable transmission of private information from a mobile device when a malicious user requests the information, or when the mobile device misestimates a security risk. The authorized user could interrupt a transmission by entering an access password to the mobile device in response to a privacy warning. When the mobile device detects activities that suggest unauthorized use, the mobile device could record or detect the activities. The recordings or detections could be used to aid the recovery of the device. For example, the device could provide location information to the authorized user as well as to the police.
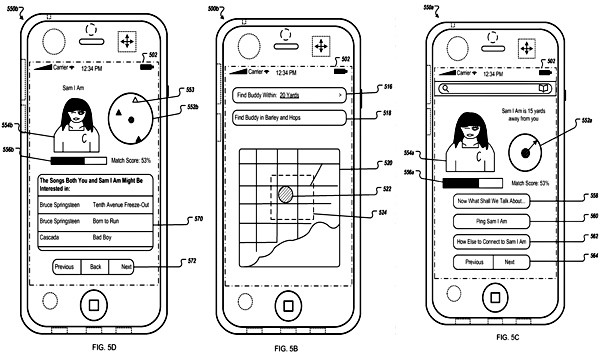
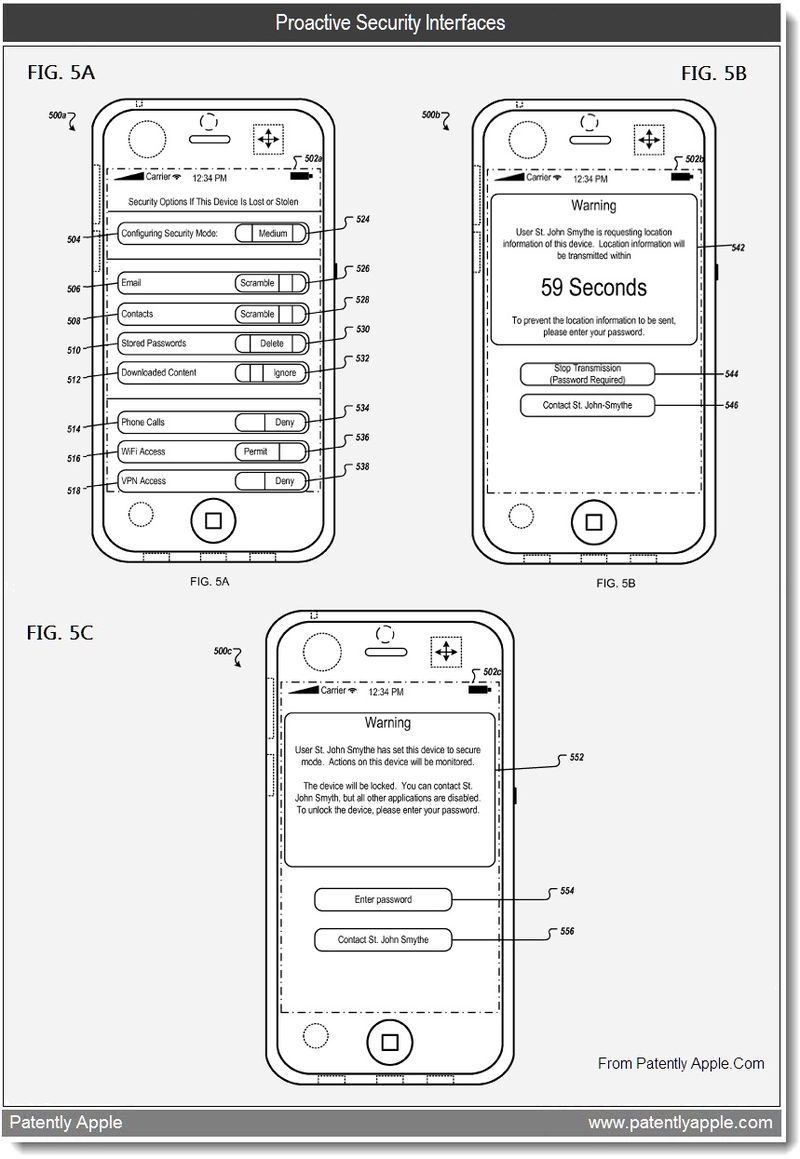
Apple‘s patent FIGS. 5A to 5C illustrate exemplary user interfaces of proactively securing mobile devices, as displayed on mobile devices. FIG. 5A illustrates an exemplary user interface that allows a user to configure security settings of mobile device 500a. The mobile device could be any present or future iOS device, according to the patent application. Apple’s patent FIG. 5B illustrates an exemplary user interface that allows a user to intervene before location information of mobile device 500b is transmitted. To protect the privacy of a user of the mobile device, it could warn the user that a transmission of location information is imminent. The warning could include a voice warning (e.g., a ring tone being played), a physical warning (e.g., mobile device 500b vibrates), or a display warning, or all of the three combined. A warning message could be displayed in a messaging area 542 on the display. The user could be given a period of time to respond. The warning message could include information on who is requesting the location information as well as a countdown to the time when the location information will be sent.
An authorized user who knows the password of the mobile device could interrupt the count down by, for example tapping on button 544 to enter the password. The user could also contact the person requesting the location by tapping button 546. Upon tapping button 546, a call could be made to a default destination number. In addition, button 546 could activate a messaging interface such that the current user of the mobile device could communicate with the requester (e.g., by opening a chat window on the mobile device and on user interface of the requester). If the current user does nothing, location information could be transmitted at the end of the countdown as indicated in messaging area. Apple‘s patent FIG. 5C illustrates an exemplary user interface that allows a user to unlock the mobile device when the mobile device is in secure operating mode. In certain security operating modes (e.g., surveillance mode), the mobile device could monitor user activities on the device, record audio snippets of conversations on phone calls of the device, and record ambient audio and digital images. Published patent application from Apple was originally filed in Q4 2009 after the original Find My iPhone feature was introduced. The sole inventor is noted as being Hooman Borghe. Also see Apple’s other security patents in Security Archives.
[ttjad keyword=”iphone”]