Do you think the passwords you use to access your most sensitive data is secure enough? Do you constantly read expert advice advice on using strong passwords but never feel you really need to, because you think your odds of getting hacked are slim? CEO of web company iFusion Labs and Internet standards expert John Pozadzides has just written an excellent piece that should make you sit up straight and take notice. This article should be on everyone’s must read list to help us better understand the security of our own passwords and how to bolster that security.
If you invited me to try and crack your password, you know the one that you use over and over for like every web page you visit, how many guesses would it take before I got it?
Let’s see… here is my top 10 list. I can obtain most of this information much easier than you think, then I might just be able to get into your e-mail, computer, or online banking. After all, if I get into one I’ll probably get into all of them.
- Your partner, child, or pet’s name, possibly followed by a 0 or 1 (because they’re always making you use a number, aren’t they?)
- The last 4 digits of your social security number.
- 123 or 1234 or 123456.
- “password”
- Your city, or college, football team name.
- Date of birth – yours, your partner’s or your child’s.
- “god”
- “letmein”
- “money”
- “love”
Statistically speaking that should probably cover about 20% of you. But don’t worry. If I didn’t get it yet it will probably only take a few more minutes before I do…
Hackers, and I’m not talking about the ethical kind, have developed a whole range of tools to get at your personal data. And the main impediment standing between your information remaining safe, or leaking out, is the password you choose. (Ironically, the best protection people have is usually the one they take least seriously.)
One of the simplest ways to gain access to your information is through the use of a Brute Force Attack. This is accomplished when a hacker uses a specially written piece of software to attempt to log into a site using your credentials. Insecure.org has a list of the Top 10 FREE Password Crackers right here.
So, how would one use this process to actually breach your personal security? Simple. Follow my logic:
- You probably use the same password for lots of stuff right?
- Some sites you access such as your Bank or work VPN probably have pretty decent security, so I’m not going to attack them.
- However, other sites like the Hallmark e-mail greeting cards site, an online forum you frequent, or an e-commerce site you’ve shopped at might not be as well prepared. So those are the ones I’d work on.
- So, all we have to do now is unleash Brutus, wwwhack, or THC Hydra on their server with instructions to try say 10,000 (or 100,000 – whatever makes you happy) different usernames and passwords as fast as possible.
- Once we’ve got several login+password pairings we can then go back and test them on targeted sites.
- But wait… How do I know which bank you use and what your login ID is for the sites you frequent? All those cookies are simply stored, unencrypted and nicely named, in your Web browser’s cache. (Read this post to remedy that problem.)
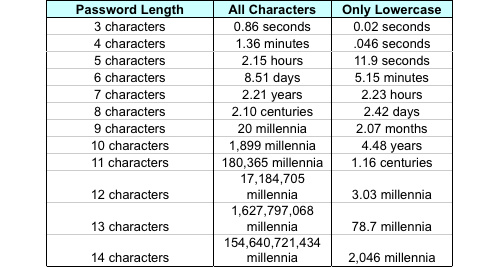
And how fast could this be done? Well, that depends on three main things, the length and complexity of your password, the speed of the hacker’s computer, and the speed of the hacker’s Internet connection.
Assuming the hacker has a reasonably fast connection and PC here is an estimate of the amount of time it would take to generate every possible combination of passwords for a given number of characters. After generating the list it’s just a matter of time before the computer runs through all the possibilities – or gets shut down trying.
Pay particular attention to the difference between using only lowercase characters and using all possible characters (uppercase, lowercase, and special characters – like @#$%^&*). Adding just one capital letter and one asterisk would change the processing time for an 8 character password from 2.4 days to 2.1 centuries.
Remember, these are just for an average computer, and these assume you aren’t using any word in the dictionary. If Google put their computer to work on it they’d finish about 1,000 times faster.
Now, I could go on for hours and hours more about all sorts of ways to compromise your security and generally make your life miserable – but 95% of those methods begin with compromising your weak password. So, why not just protect yourself from the start and sleep better at night?
Believe me, I understand the need to choose passwords that are memorable. But if you’re going to do that how about using something that no one is ever going to guess AND doesn’t contain any common word or phrase in it.
Here are some password tips:
- Randomly substitute numbers for letters that look similar. The letter ‘o’ becomes the number ‘0′, or even better an ‘@’ or ‘*’. (i.e. – m0d3ltf0rd… like modelTford)
- Randomly throw in capital letters (i.e. – Mod3lTF0rd)
- Think of something you were attached to when you were younger, but DON’T CHOOSE A PERSON’S NAME! Every name plus every word in the dictionary will fail under a simple brute force attack.
- Maybe a place you loved, or a specific car, an attraction from a vacation, or a favorite restaurant?
- You really need to have different username / password combinations for everything. Remember, the technique is to break into anything you access just to figure out your standard password, then compromise everything else. This doesn’t work if you don’t use the same password everywhere.
- Since it can be difficult to remember a ton of passwords, I recommend using Roboform for Windows users. It will store all of your passwords in an encrypted format and allow you to use just one master password to access all of them. It will also automatically fill in forms on Web pages, and you can even get versions that allow you to take your password list with you on your PDA, phone or a USB key. If you’d like to download it without having to navigate their web site here is the direct download link. (Ed. note: Lifehacker readers love the free, open-source KeePass for this duty, while others swear by the cross-platform, browser-based LastPass.)
- Mac users can use 1Password. It is essentially the same thing as Roboform, except for Mac, and they even have an iPhone application so you can take them with you too.
- Once you’ve thought of a password, try Microsoft’s password strength tester to find out how secure it is.
By request I also created a short RoboForm Demonstration video. Hope it helps…
Another thing to keep in mind is that some of the passwords you think matter least actually matter most. For example, some people think that the password to their e-mail box isn’t important because “I don’t get anything sensitive there.” Well, that e-mail box is probably connected to your online banking account. If I can compromise it then I can log into the Bank’s Web site and tell it I’ve forgotten my password to have it e-mailed to me. Now, what were you saying about it not being important?
Often times people also reason that all of their passwords and logins are stored on their computer at home, which is safe behind a router or firewall device. Of course, they’ve never bothered to change the default password on that device, so someone could drive up and park near the house, use a laptop to breach the wireless network and then try passwords from this list until they gain control of your network — after which time they will own you!
Now I realize that every day we encounter people who over-exaggerate points in order to move us to action, but trust me this is not one of those times. There are 50 other ways you can be compromised and punished for using weak passwords that I haven’t even mentioned.
I also realize that most people just don’t care about all this until it’s too late and they’ve learned a very hard lesson. But why don’t you do me, and yourself, a favor and take a little action to strengthen your passwords and let me know that all the time I spent on this article wasn’t completely in vain.
Please, be safe. It’s a jungle out there.
Source: onemansblog.com




Pingback: Albert
Pingback: http://%/bvyhrdt4
Assuming the hacker has a reasonably fast connection.
omg you are an idot it’s posable to hack any password no matter how good it is a program that sends the code to the program or password sucrity it’s like picing a lock now you bild a loop that counts to infinity example every letter you type useing the key bord even the dalor sing are binary number coded like 01100001 is the leter “a” i do not nead a translator when i allready know now if you count though numbers that mean evry possable word like “hi”=104 105 in decanal numbers now you convert it to binary you get 01101000 01101001 thats in the binary format evry 8 binary digits is a byte and thay are stored in flip flop circuts in the computer and use data slecting circuts to get to each byte now useing counting you can get any possable combination there is for a password and heres one thing i bet your not awear of your internet company by law are to whatch for every computer and any thing done is allso stored in a log so basicaly it’s allmost imposable to get awhay with anything unless you mutly task you computer 2 times and control what thay see on one side of it and make the other connect to a diffrent internet from a vary far awhay place i only know this stuff i will naver use any of it though but that gives you the idea that if you know how everything works in a computer it’s just as easy to reverse it bild a counting program and have it increse by 1 size each time it’s not let though have it go though all the leters and numbers of the althabet and have it enter them after all leters or numbers are went though for a 1 digit password up it to 2 and have it do the fist letter of the password or number than the last digit changes each time all leters and numbers went though this can be done with an allgritham and you do not nead to store the letters into a sting write a binary code that runs the codes for the processor in that digital device and have it count if you add 1 to a binary number each time it auto maticaly gos though all possible byte combinations set the bytes in parwell and have it increase if the password combinations will not go though with a fast computer this can be done vary fast every letter you type are binary coeds from the key bord now you get it there is no real whay to portect your self and this will alert people of how easy it is with a vary simple simple code that sends bytes though the key bord and enters the password all the garbage on the internet makes me angry i know every thing about digital as it is i bilt a circut that add’s without electrisity light is also a enagy like electristy but is much faster all this tecnolagy will be trash in the futer any whays if you wish to ask qestions or just simpaly what to know more just ask my email is stored when i send this i will tell you right now i dispize hacking i don’t like it becuase most people that do any thing remotly to what i know hide so well it’s imposable to find them even though the intrent simple trick biltd your owne reciver and transmiter that works drectly off the stalites show it’s location some place half whay around the world rght now meny people are beaing acused of hacking even though thay did nothing most people that hack do it to distory shit and i dispize hacking i mostly like to ceap the not know much act and i realy use shity computers and there pertending that everything is private well here is another thing people are not awear of every time you transmit a signal to get data off the intrnet is stored in log files pluse it’s monotored all the time and you get paid good monny but it gets vary boring watching people banking as a job online and digital computers are nothing more than switches thay only understand a logic such as 1 or 0 but diffrent whays there put can be folowed by instuctions and numbers and graphics with the processor acting as something you would think of as a command prompt every thing in digital is all based by off and on with circuts based off that hooked up to electrical componets computers are shit tecnolagy is shit i know every thing about them but all it is is shit fuck it all i even though awhay my computer at one time i use it just not offten and i only use it for what i have to and i allyes make shere im not connected to the internet when i do not nead the internet nothing but freqancy readation satalites focusing it to one stead steam back down to earth where it decodes as high and low as 1 and 0 agen nothing but radeaation fucking shity tecnoligic world with all this people will loose there abilatlys to conunicate to other people and to see live concerts becuase of all this shit i fucking hate it all people becoming lazy and usless becuase every thing dose every thing for them
Pingback: Private Servers
Poo is nice on cake
please email me.
i really need help with a hack
i could really REALLY use your help
mybabie12@gmail.com
Thanks for information. that tells how can you hack weak passwords
http://www.webinsect.com/
However, what we are rarely taught in school is just how much logical reasoning may be necessary in the jobs we do in later life. In fact, reasoning is often the driving force behind many processes in many departments of almost all businesses.
Okay, the suggestion of substituing numbers for letters, “5” for “s”, for example, is idiotic. How many people do you think do that and think it’s a clever way of making their passwords stronger? Answer: a lot. How useful is it? Answer: not very.
If people substitute 1 for L and I then it’s really not hard to just quickly try common letter substitutions in a password cracking program. As in so easy that even the basic piece of software my company uses for security testing has one built in.
If you want a secure password then the simplest thing is to pick a long one. Ideally, pick a mental image and then just use that as your password, e.g. “punchadolphinday”. That’s all lower case and it’s easily memorable – but it’s much, much, harder to crack than “Mod3lTF0rd” – which anyone using a word list with a decent mutations code should be able to crack in just a few hours. On the other hand, the same program might take months or years to crack “punchadolphinday”. That’s because it’s a random collection of words, to a computer’s perspectives, and not a common password with predictable numbers thrown in in predictable places – like “Mod3lTF0rd” is.
Derekslogar1@hotmail.com message me i need help also
YouTube have started to convert their movies so that they will work on the iPhone, but because of the amount of files on their website this is going to take time. The YouTube app works fine but I find that often the videos that I search for don’t appearin the way they would if you search online. An example of this is if you searched for “The Beatles” then you would get a ton of song covers before any of the songs performed by The Beatles.