In the world of operating systems, Windows 8 is still a relatively new entry. Not so, though, for malware authors who have been quick to add ‘support’ for the new OS to their malwares. This is the case with a newly-discovered Trojan Backdoor.Makadocs which uses Google Docs to contact its control server.
Symantec discovered the malware recently and according to the company, it contained additional clauses to its original code which let it target Windows 8 machines, although its functionality hasn’t been enhanced to let it accomplish such a feat.
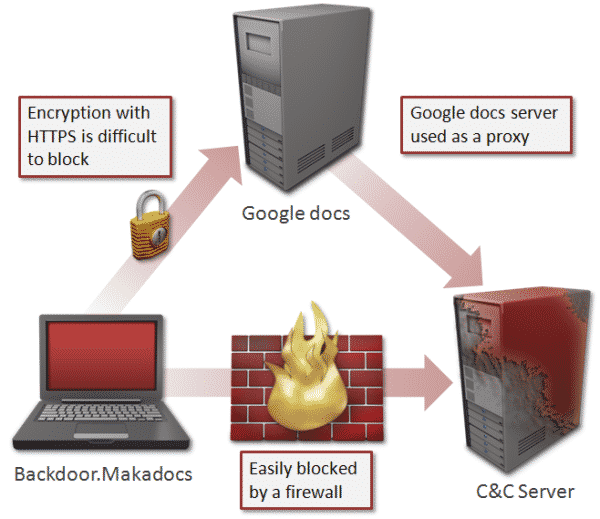
The authors of the malware are trying to spread it via a Microsoft Word document titled ‘Trojan.Dropper.’ What is very interesting about this malware is that to contact its command and control server(C&C), it makes use of Google Docs.
Google Docs is a very popular service used by millions of people. The malware exploits this by making use of the Google Docs to contact the control server and then take further directions from it. It couldn’t directly contact the C&C because of a firewall or any other security mechanism in place. But any communication through Google Docs is encrypted.
The data then is encrypted and sent over to the Google Docs server by this malware. This data is then forwarded by the Google Docs server to the original C&C. It is indeed a clever social engineering move by the malware authors. However, now that Google has been made aware of it, the company can take measures to ensure that the malware is no longer able to manipulate Google Docs.
Source: Symantec
Courtesy: TNW
[ttjad keyword=”cloud-storage-drive”]