Anonymous hackers associated with the AntiSec movement taunted Apple over the weekend by posting a list of 27 usernames and passwords, pwned data apparently originated from a number of surveys hosted on an Apple business website. Anonymous have claimed to have breached one of Apple’s servers and have managed to gain access to private data. There has been no word from Apple regarding this matter and hackers apparently are too busy elsewhere to mess with Apple, but that doesn’t mean the company is bulletproof………..
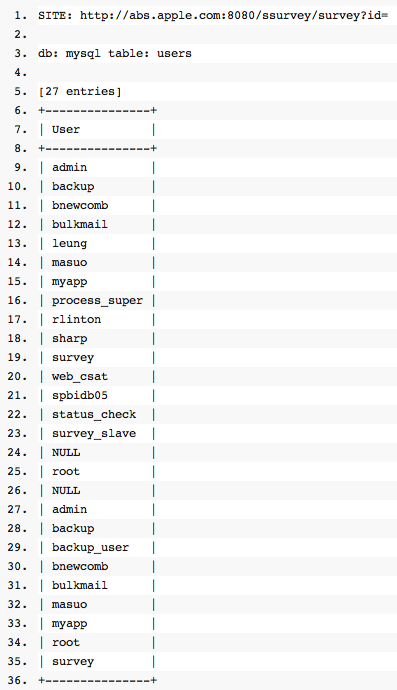
A few weeks ago the online hacktivist group Anonymous and members from the now-defunct Lulz Security joined forces under the AntiSec operation (short for anti-security), declaring war against governments and giant corporations in the name of the public good. AntiSec posted a message on Twitter claiming they had gained access to private data from an Apple server. To back their claims up, the group posted the usernames and passwords for 27 root and admin accounts from the users table in a MySQL database. The breached server is used by the Cupertino giant to conduct technical support follow-up surveys, and according to early reports it doesn’t seem that any customer data was compromised. The WSJ is reporting that the AntiSec hackers that have been joyriding around the internet using SQL injectors to steal username and password have hit Apple’s servers and taken usernames and passwords.
The hackers said in a statement posted to Twitter that they had accessed Apple’s systems due to a security flaw used in software used by the Cupertino, Calif.-based gadget maker and other companies. “But don’t worry,” the hackers said, “we are busy elsewhere.” A spokesman for Apple didn’t immediately respond to a request for comment. The posted information comes as part of a two-month campaign of digital heists targeting corporations including Sony Corp. and AT&T Inc., as well as government agencies such as the U.S. Senate, the Central Intelligence Agency and the Arizona Department of Public Safety.
Specifically, they say they’ve got the username and passwords from this server:
http://abs.apple.com:8080/ssurvey/survey?id=
While this looks to be a pretty harmless server with only local usernames, previous postings have claimed a much bigger bounty:
Some weeks ago, we smashed into the iCloud with our heavy artillery Lulz Cannons and decided to switch to ninja mode. From our LFI entry point,we acquired command execution via local file inclusion of enemy flee. Apache vessel. We then found that the HTTPD had SSH auth keys, which let our ship SSH into other servers. See where this is going?We then switched to root ammunition rounds.And we rooted… and rooted… and rooted…After mapping their internal network and thoroughly pillaging all of their servers, we grabbed all their source code and database password which we proceeded to shift silently back to our storage deck.
[ttjad keyword=”mac”]