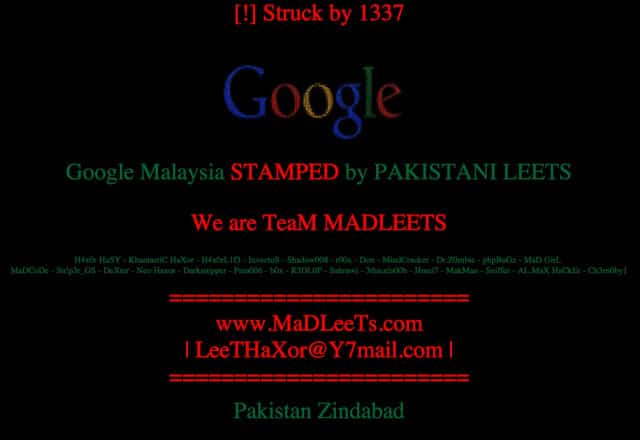
In recent months, we have seen a number of DNS poison attacks. These attacks typically involve meddling with the DNS of a given site so that it is redirected by the hackers to a different page. A similar attack has now been used to hack and redirect Google’s Malaysian site.
The credit for this fresh DNS attack has been claimed by a group of hackers which apparently goes by the name ‘Team Madleets.’ As a result of the DNS poison attack, the site was unavailable for several hours and users trying to visit it were redirected to a typical splash screen where hackers claimed credit.
To orchestrate the attack, the team of hackers behind it somehow accessed the Malaysian Network Information Center. Once they had the access, they were able to change the DNS settings of Google’s Malaysian site. Interestingly, the hackers who have accomplished this seem to have done it for no apparent reason.
The Facebook page of ‘Team Madleets’ explains the motive behind the attack in these words:
“We feel we need to alert anyone, that we don’t hack any country tlds for example google.com.my as a result of any kind of hate, We don’t hate anyone, We love all humanity, there is no obvious reason for stamping the tlds.
Least the reason is not any kind of hate.
Whatever the reason is we can’t explain except we love all of you.
Regard’s
H4x0rL1f3.”
In other words, these hackers pulled off the attack simply for the heck of it, although conventionally such attacks have political basis. After being offline for hours, access to Google’s Malaysian domain has been restored.
Courtesy: TechCrunch
[ttjad keyword=”all-in-one-desktops”]