Microsoft Security Response Center (MSRC) Engineering has concluded that WebGL, the royalty free cross-platform API for browser-based 3D graphics is overly permissive, insecure and potentially harmful to machines using it, development of the technology was spearheaded by Mozilla, Google, Opera, AMD, and Nvidia. WebGL is the 3D rendering standard used in both Chrome and Firefox and can be turned on in Apple’s Safari browser, it turns out the technology has a flaw, allowing hackers low level access to graphics cards and possible entry to grab at user’s data. The Cupertino crew plans to bring WebGL to iOS 5 with one very strange restriction and it will only be available to iAd developers. It will eventually be opened up in mobile Safari for everyone, but for the moment it seems browser-based 3D graphics will be limited to advertisements on the iPhone…………
Microsoft looks set to sink one of the most exciting features of the new web that we tend to label HTML5 and WebGL is a standard for creating 3D graphics in a web page – within a Canvas object to be precise. It is a finalized standard but at the moment only Chrome and FireFox support and it’s clear that to be an accepted standard either IE has to also support it or IE has to become a forgotten hardly used browser. Microsoft said that it refuses to endorse WebGL from a security perspective and the strong words came directly from Microsoft’s own security research and defines team. Microsoft’s MSRC engineering team has been analysing WebGL recently and concludes that Microsoft products supporting WebGL would “have difficulty” passing the company’s own Security Development Lifecycle requirements. The software giant highlighted the following concerns in a blog post on Thursday:
- Browser support for WebGL directly exposes hardware functionality to the web in a way that we consider to be overly permissive:
- Browser support for WebGL security servicing responsibility relies too heavily on third parties to secure the web experience:
- Problematic system DoS scenarios:
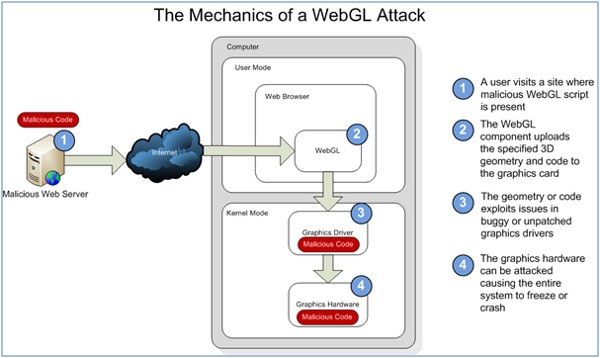
The security of WebGL as a whole depends on lower levels of the system, including OEM drivers, upholding security guarantees they never really need to worry about before. Attacks that may have previously resulted only in local elevation of privilege may now result in remote compromise. While it may be possible to mitigate these risks to some extent, the large attack surface exposed by WebGL remains a concern. We expect to see bugs that exist only on certain platforms or with certain video cards, potentially facilitating targeted attacks.
As WebGL vulnerabilities are uncovered, they will not always manifest in the WebGL API itself. The problems may exist in the various OEM and system components delivered by IHV’s. While it has been suggested that WebGL implementations may block the use of affected hardware configurations, this strategy does not seem to have been successfully put into use to address existing vulnerabilities.It is our belief that as configurations are blocked, increasing levels of customer disruption may occur. Without an efficient security servicing model for video card drivers (eg: Windows Update), users may either choose to override the protection in order to use WebGL on their hardware, or remain insecure if a vulnerable configuration is not properly disabled. Users are not accustomed to ensuring they are up-to-date on the latest graphics card drivers, as would be required for them to have a secure web experience. In some cases where OEM graphics products are included with PCs, retail drivers are blocked from installing. OEMs often only update their drivers once per year, a reality that is just not compatible with the needs of a security update process.
Modern operating systems and graphics infrastructure were never designed to fully defend against attacker-supplied shaders and geometry. Although mitigatinos such as ARB_robustness and the forthcoming ARB_robustness_2 may help, they have not proven themselves capable of comprehensively addressing the DoS threat. While traditionally client-side DoS is not a high severity threat, if this problem is not addressed holistically it will be possible for any web site to freeze or reboot systems at will. This is an issue for some important usage scenarios such as in critical infrastructure.
Microsoft believes that WebGL will become an ongoing source of hard-to-fix vulnerabilities in its current form. The software maker says that, in its current form, WebGL is not a technology Microsoft can endorse from a security perspective. The company recognises the need to provide solutions for WebGL but says that its goal is that such solutions are secure by design, secure by default, and secure in deployment. WebGL (Web-based Graphics Library) is a new software library that extends JavaScript to allow 3D interactive graphics within any compatible browser. Mozilla Firefox, Google Chrome and upcoming versions of Safari and Opera all support WebGL. The software library is managed by non-profit technology consortium Khronos Group. Microsoft also contends that the use of WebGL enables denial-of-service scenarios that would make it possible for any web site to freeze or reboot systems at will. In an e-mailed statement, Ari Bixhorn of Microsoft’s Internet Explorer team took a direct swipe at its competition:
“Customers need to understand that the security of their computers is at risk when they browse the web using Google Chrome and Firefox. Because these browsers support WebGL, they open a door for malicious websites to access one of the most secure parts of a person’s computer. With security holes like this, it’s clear that WebGL isn’t ready for primetime, and that people shouldn’t be using a browser that supports it. This is why the Microsoft Security Response Center recently recommended against the use of WebGL in Microsoft products like Internet Explorer.”
In a response to other media outlets, Khronos Group downplays security concerns, suggesting that browser vendors are still working toward passing a WebGL conformance suite and that the demonstrated security issue is due to a bug in Firefox’s WebGL implementation. That bug is reportedly resolved in Firefox 5, which is due for release before the end of the month. A Khronos Group spokesperson declined to respond directly to Microsoft’s report but noted that Mozilla, Firefox and Opera all strongly support WebGL and also Apple has announced limited support for WebGL in iOS 5. A Google spokesperson said the company doesn’t see WebGL as a significatn threat to its users. Many parts of the WebGL stack, including the GPU process, run in separate processes and are sandboxed in Chrome to help prevent various kinds of attacks, the spokesperson added. Google says it can ward off lower level attacks by working with hardware, OS and driver vendors to disable WebGL on system configurations that are found to be unsafe.
[ttjad keyword=”microsoft”]


![Read more about the article Lumi Process: A Revolutionary Fabric Print Process Using Sunlight [Kickstarter]](https://thetechjournal.com/wp-content/uploads/2012/07/inkodye-512x495.jpg)
