Earlier this year, we reported about a nefarious malware that had been discovered by Kaspersky Labs. The malware, called Flame, was deemed the most complex malware that has been seen to date. Researchers have since been looking into its details and have been able to find the nicknames of the coders who were behind the malware.
Ever since its discovery, it has been believed that Flame is an espionage tool that has been created through nation-state support, quite probably by US and Israel. Researchers have been looking into the data that was found on the command-and-control servers of the malware and have found a number of new clues.
For instance, they have found evidence that the team behind this malware was working on it ever since 2006 and perhaps even before that. This is definitely unsettling for the security companies as well as the online community since it means that Flame malware was able to thwart any kind of detection for many years.
It has also been discovered that there are at least three other variants of Flame which are as yet undiscovered and may be out in the wild, infecting machines without being detected. This, again, is disturbing news since we’ve already seen what Flame is capable of.
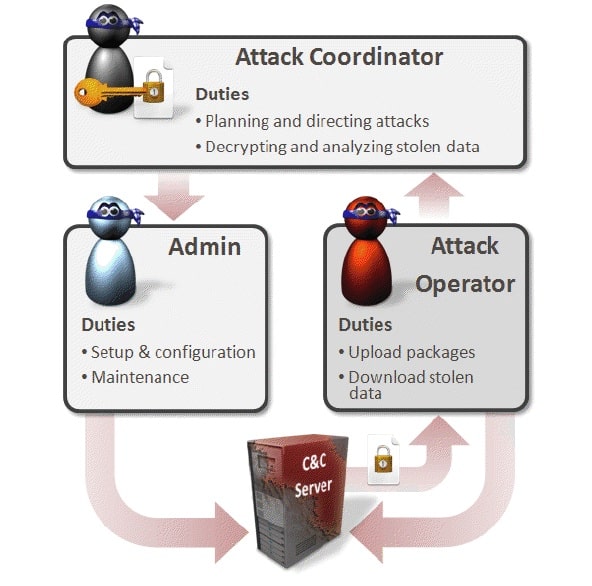
Finally, the servers contained nicknames of the coders who are behind the Flame malware. Symantec and Kaspersky have been collaborating on this research and have came across these nicknames. The names haven’t been made public for security reasons although they have been denoted as D, H, O and R.
The clues on the servers clearly show that ‘H’ was probably the team lead, handling the most complex data encryptions whereas ‘O’ and ‘R’ were responsible for handling the MySQL database.
Courtesy: Wired
[ttjad keyword=”cloud-storage-drive”]