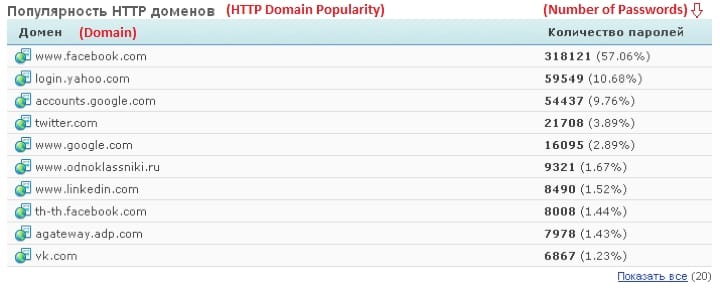
Most major tech companies such as Facebook and Twitter pride themselves in the advanced security features of their sites. Despite these, a botnet was recently able to nick away some 2 million passwords of Facebook, Google, Twitter and ADP accounts.
The botnet in question apparently relied on a malware program to infect the victims. The program was able to spread to hundreds of thousands of machines. Once it was inside the machine, the program would communicate with a Netherlands-based command-and-control server which would receive the user login information from each infected machine.
In total, reports have it that 318,121 Facebook login credentials and 59,549 Yahoo login credentials were stolen. Google also made the list with the malware having nicked credentials of some 54,437 Google accounts.
The most worrisome part of this entire botnet is that it was apparently able to gain access to ADP systems. ADP is a notable organization which specializes in payroll systems, controlling the monthly paychecks of countless people in the U.S. Trustwave’s SpiderLabs revealed that ADP accounts were also compromised by the botnet which communicated the data it gathered back to its server. The software used by this huge botnet was nicknamed ‘Pony.’ Facebook and Yahoo have apparently reset the passwords of the compromised accounts while Google hasn’t responded to the news yet. ADP, on the other hand, has stated that it has found no evidence of a malware on any of its machines.
Commenting on the method of the attack by ‘Pony’, Daniel Chechik of SpiderLabs said “This technique of using a reverse proxy is commonly used by attackers in order to prevent the command-and-control server from being discovered and shut down—outgoing traffic from an infected machine only shows a connection to the proxy server, which is easily replaceable in case it is taken down.”
Source: SpiderLabs
Courtesy: PC World
[ttjad keyword=”htc-phones”]