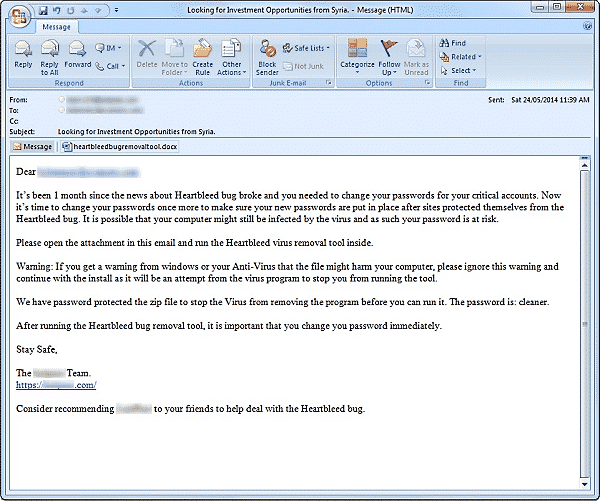
We extensively covered the vulnerability in the OpenSSL protocol that put three-quarters of the internet at security risk recently and came to be known as ‘Heartbleed.’ Now, a malware is being spread masquerading as a ‘Heartbleed Bug Removal Tool.’
Heartbleed itself is a vulnerability, not a virus which infects machines. In simpler words, it is simply a security loophole in the otherwise secure OpenSSL protocol. So the only solution to such a vulnerability was to patch it up in a subsequent version, which OpenSSL did.
But a new spam campaign is trying to fool the naive users. Through extensive email spamming, people are told that the Heartbleed has ‘infected’ their machine and that they must run the bug removal tool in order to get rid of the virus. Attached to the email is what looks like a docx file, which many unwitting users download. Upon download, it turns out to be a zip file and once the file is unzipped, it contains a malicious.exe file which is shown as the real bug removal tool.
If a user runs malicious.exe, it automatically downloads an invisible keylogger in the background. At the same time, a progress bar appears on the screen which, upon completion, tells the user that his machine is not infected with the Heartbleed bug and that it’s safe. Meanwhile, the keylogger is in place and any keystrokes that the user enters on his machine are then recorded by the software. This makes the login information of online accounts, personal information, financial details and other data on that machine available to the authors of the malware.
Source: Symantec
[ttjad keyword=”all-in-one-desktops”]