The war on terror has been going on for a while now. And though U.S. has claimed many victories in it, such as the elimination of Osama bin Laden, the war seems far from over. A group of researchers from West Point have devised a new algorithm which, they claim, can help defeat the terrorists more effectively.
The algorithm, in itself, takes into account individual terrorist organizations. And it also makes some basic assumptions. Paulo Shakarian, who heads this team of researchers, is of the opinion that recent data shows how different terrorist organization such as Al-Qaida is highly decentralized. This makes it extremely hard for them to be eliminated.
The moment the head of the organization is eliminated, a new person is appointed and thus, little is gained. Shakarian proposes that by forcing such an organization to become more centralized, anti-terrorist agencies can dismantle and disrupt them far more easily.
According to him, an effective way of doing this could be to eliminate the middlemen which would force powers into a few hands, possibly the lead person. And then take that lead person out so that the rest of the organization is left helpless and has to disperse.
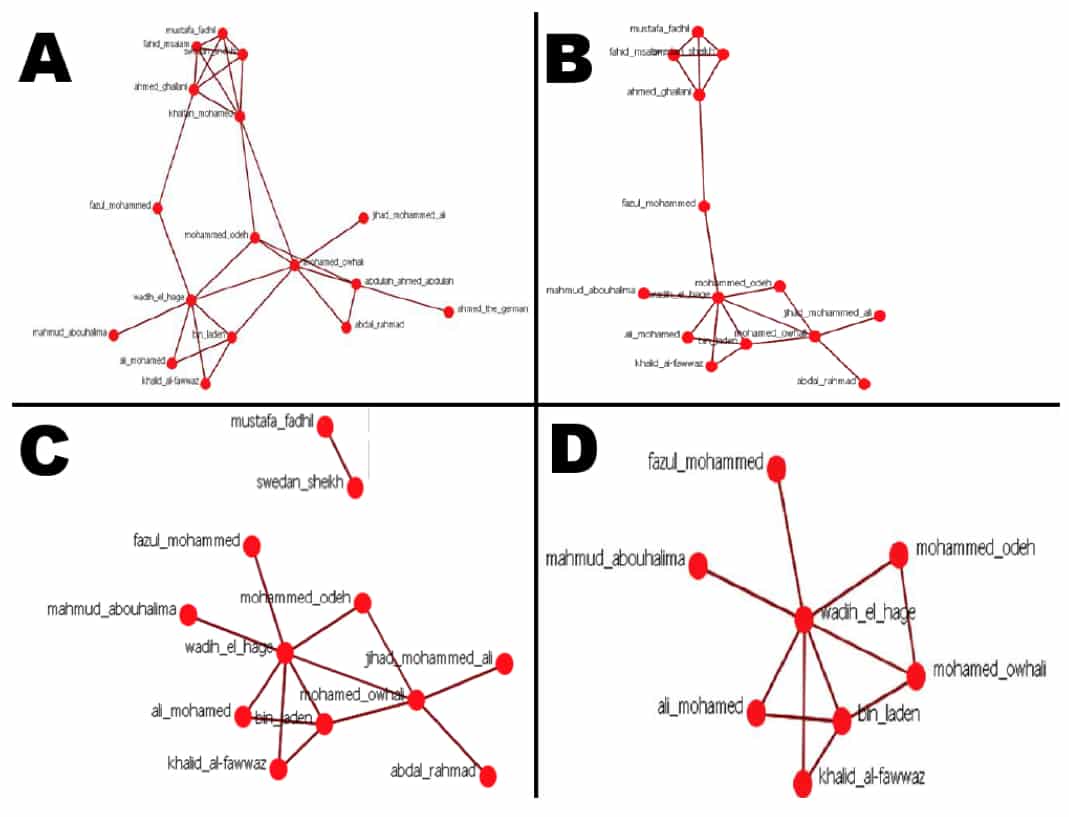
Based on this theory, Shakarian was able to come up with an algorithm which is called GREEDY_FRAGILE and has been written in Python. The algorithm essentially shows such nodes in a terrorist organization which can be manipulated to make the organization more centralized. The researchers made use of some real-world examples to demonstrate this and according to them, “In each of the five real-world terrorist networks that we examined, removal of only 12% of nodes can increase the network-wide centrality between 17% and 45%.”
Obama administration claims that it makes use of a special social-network analysis to see which terrorists ought to be targeted through drone attacks. An intelligent algorithm such as GREEDY_FRAGILE, authors argue, can help the administration pin such targets which can help eliminate the entire organization in the long run.
Source: Cornell University Library
Courtesy: Wired
[ttjad keyword=”chrome-laptop”]