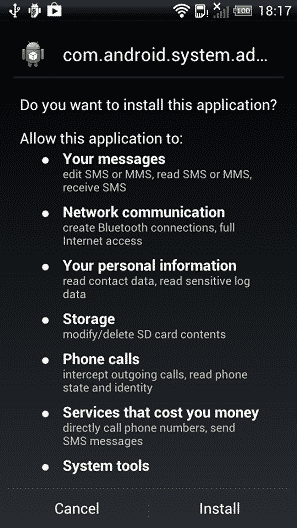
A number of Android trojans have surfaced in recent months, given the fact that the platform is an easy target. Kaspersky Lab has now identified a new trojan which is considered the most sophisticated Android trojan to date. It is named ‘Obad.a’ and makes use of a number of as-yet-unidentified Android bugs.
The complete name of the trojan is Backdoor.AndroidOS.Obad.a. It can not only sneak into a handset rather discreetly, it can even expand to other nearby handsets through Bluetooth and Wi-Fi. Once a handset is infected, it lets the attacker leverage the handset to send out more malicious text messages, thereby seeking access to more devices.
According to a post written by Roman Unuchek of Kaspersky Lab, ‘To conclude this review, we would like to add that Backdoor.AndroidOS.Obad.a looks closer to Windows malware than to other Android trojans, in terms of its complexity and the number of unpublished vulnerabilities it exploits. This means that the complexity of Android malware programs is growing rapidly alongside their numbers.’
Interestingly, the point of infection of this trojan is not through any of Android apps. Rather, it spreads through malicious text messages, which is far more handy and convenient for the attackers. Many users tend to fall victim to malicious text messages, unaware how such an SMS can infect their device.
As soon as the trojan is inside an Android device, it is able to connect to a command-and-control server and upload sensitive user data such as phone number, carrier name, IMEI number, account balance as well as the MAC addresses of any devices that are connected to the infected handset.
The trojan essentially hints that it is the work of a highly sophisticated hacking team which was able to not only create such an advanced piece of malicious software, but did so while exploiting such Android bugs which hadn’t been uncovered so far.
Source: Kaspersky Lab
Courtesy: Arstechnica
[ttjad keyword=”android-phone”]