A hacker has discovered a critical vulnerability in Gmail password reset system, enabling him to nick away Gmail passwords through simple spear-phishing attacks.
The vulnerability has been found by a security researcher, Oren Hafif. He posted a proof-of-concept video online, showing off many different exploits that he used in hacking the Gmail account of another user.
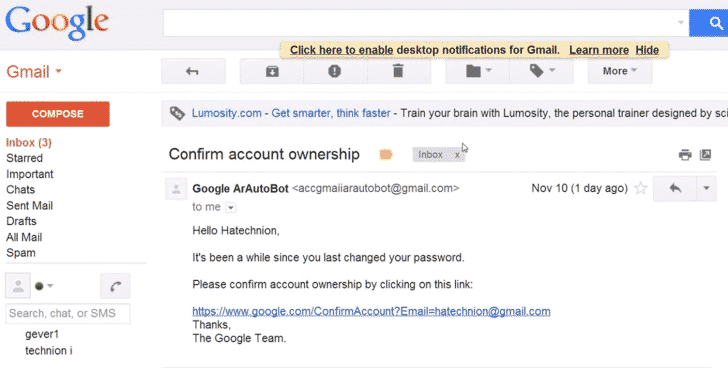
The tricks and hacks that he used in staging this Gmail password hack include a phishing attack, Cross-Site Request Forgery (CSRF) and cross-site scripting (XSS). To get the ball rolling, the attacker initially sends an email titled ‘Confirm account ownership’ to the victim. The email appears to have come from Google when in real, it is simply a phishing attack.
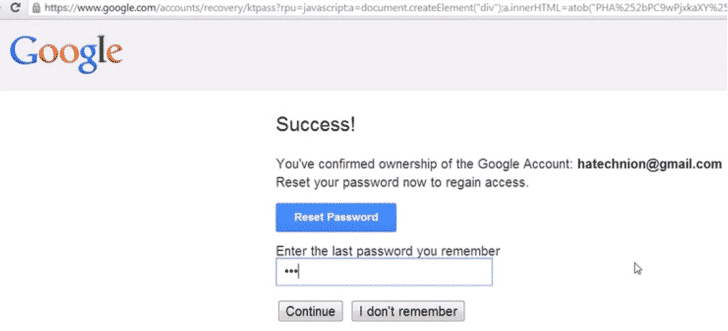
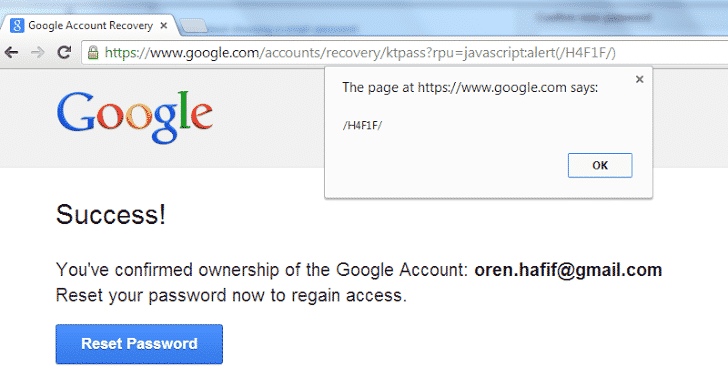
As soon as the victim hits the link provided in the email, he is taken to what appears to be an https://google.com link. But when you enter the password on the ‘Reset Password’ page, you are taken to the website of the hacker. This is done through a CSRF attack. Once you are there, the hacker has access to not only your password but also the cookies with the help of an XSS attack.
The important thing to note here is that in attempting this hack, Hafif relied on a serious security vulnerability in Google. Google, in turn, has acknowledged the vulnerability, awarded Hafif $5100 and patched the exploit before any nefarious hackers can make use of it. You can watch the demo video posted below.
Source: Oren Hafif
Courtesy: The Hacker News
[ttjad keyword=”android-device”]