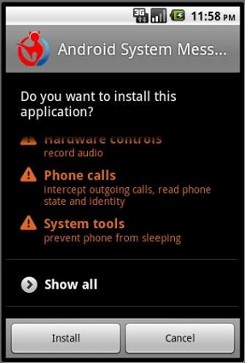
The increase in the number of applications that have come up on the Android marketplace has opened up newer avenues for developers to ear and present content to the Android community, but the dark side of the fact is that the rise in the number of applications has also opened up opportunities for cyber criminals to invent newer ways to catch hold of confidential user data and a newest security threat has been identified for Android users, the Trojan or a malicious program disguised as an application has found out to be recording conversations that users do using their smartphones. The Trojan activates itself and records ever conversation that takes place on the device in a low quality audio format so that the user does not even have a clue about it and after the call is complete the Trojan then can easily send the file through an email to any email address as an attachment……………….
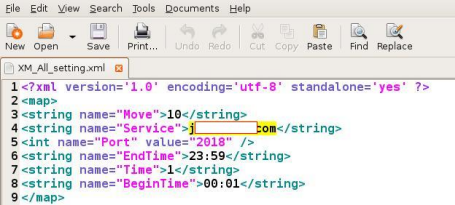
There’s a new Android trojan in town and it’s secret weapon is the ability to record your phone conversations. At least, that’s what CA Technologies’ Dinesh Venkatesan claims in his latest blog. According to the report, the malware drops a configuration file, one that contains key information about the remote server and the parameters — once it’s installed on the victim’s device. It then records and stores phone conversations in AMR format on the consumer’s SD card. Based on the configuration file, it’s assumed that the trojan also has the ability to upload these conversations to a remote server maintained by the trojan‘s author.The news is a step up from last week’s report of a trojan that logged details of incoming and outgoing phone calls, and their duration. Venkatesan didn’t say how he came across the new malicious package, but explains that he tested the eavesdropping malware in “a controlled environment with two mobile emulators running along with simulated Internet services.” One screenshot confirms that the malware must ask permission before installing itself on the device, emulating a legitimate app. “Making a phone call from the victim device to trigger the payload,” reads one screenshot caption. “As the conversation goes on, the Trojan stores the recorded call in a directory shangzhou/callrecord in the SD Card. “The file was saved as 0110731012842001.amr and could be played back in VLC Media Player. The actual size of the audio file wasn’t given. As it is already widely acknowledged that this year is the year of mobile malware, we advice the smartphone users to be more logical and exercise the basic security principles while surfing and installing any applications,” he said. Of course, that’s easier said than done when consumers place their trust in Google and assumes that the search engine giant is on the ball by filtering out any disguised malware lurking on the Android Market. And while Android has the upper hand over Apple’s iOS in terms of development freedom, installing apps from outside the Android Market / Amazon Appstore circle is certainly risky business.
[ttjad keyword=”general”]



BEWARE: New Android Malware as Google+ App http://bit.ly/qaSJuz