Google’s Web mapping appears to be able to track your phone within feet of your actual location in yet another wrinkle in the ongoing location-based services and privacy debate that will now hit Congress, if someone knows a hardware ID, they may be able to find your physical address. Only Google and Skyhook Wireless make their location databases linking hardware IDs to street addresses publicly available on the internet, which raises novel privacy concerns when the IDs they’re tracking are mobile………….
If you have Wi-Fi turned on, the previous whereabouts of your computer or mobile device may be visible on the Web for anyone to see. Google publishes the estimated location of millions of iPhones, laptops and other devices with Wi-Fi connections, a practice that represents the latest twist in a series of revelations this year about wireless devices and privacy, CNET has learned. Android phones with location services enabled regularly beam the unique hardware IDs of nearby Wi-Fi devices back to Google, a similar practice followed by Microsoft, Apple and Skyhook Wireless as part of each company’s effort to map the street addresses of access points and routers around the globe. That benefits users by helping their mobile devices determine locations faster than they could with GPS alone. Only Google and Skyhook Wireless, however, make their location databases linking hardware IDs to street addresses publicly available on the Internet, which raises novel privacy concerns when the IDs they’re tracking are mobile. If someone knows your hardware ID, he may be able to find a physical address that the companies associate with you or even if you never intended it to become public.
Tests performed over the last week by CNET and security researcher Ashkan Soltani showed that approximately 10 percent of laptops and mobile phones using Wi-Fi appear to be listed by Google as corresponding to street addresses. Skyhook Wireless‘ list of matches appears to be closer to 5 percent. “I was surprised to see such precise data on where my laptop–and I–used to live,” says Nick Doty, a lecturer at the University of California at Berkeley who co-teaches the Technology and Policy Lab. Entering Doty’s unique hardware ID into Google’s database returns his former home in the Capitol Hill neighborhood in Seattle. Wi-Fi-enabled devices, including PCs, iPhones, iPads and Android phones, transmit a unique hardware identifier, called a MAC address, to anyone within a radius of approximately 100 to 200 feet. If someone captures or already knows that unique address, Google and Skyhook‘s services can reveal a previous location where that device was located, a practice that can reveal personal information including home or work addresses or even the addresses of restaurants frequented.
A Google spokesman would not answer whether Android phones or Street View cars have collected the MAC addresses of phones or computers not acting as Wi-Fi access points–a practice that, if true, would pose a greater privacy risk. Skyhook Wireless CEO Ted Morgan says that his company only collects access point addresses. Doty says that his computer may have been used as an access point for testing, but “I certainly didn’t do so commonly.” Alissa Cooper, chief computer scientist at the Center for Democracy and Technology and co-chair of an Internet Engineering Task Force on geolocation, says that her laptop was never used as a Wi-Fi access point. Her previous street address off of Connecticut Avenue in Washington, D.C., where she lived from 2007 to 2009, nevertheless shows up in Google‘s location database. Over the course of a minute in a coffeehouse in San Francisco’s Mission district, the unique MAC addresses of 76 computers using Wi-Fi connections were visible. Seven appeared in Google‘s database with corresponding street locations, and three appeared in Skyhook‘s.
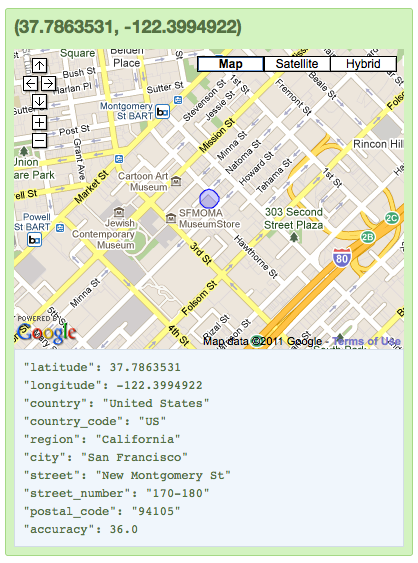
The locations corresponding to the MAC addresses visible in San Francisco were all over the map. An Apple device visible in the coffeehouse had a street address of Grouse Lane in Woodbridge, Conn., meaning it was previously recorded as being present there. Another was listed as being a few miles away, near 170 New Montgomery St. A third was spotted in Los Altos, Calif., and a fourth in Berlin. Google’s location database also can be be used, in a few cases, to track movements. One HTC device connecting to the South of Market Wi-Fi hot spot on Wednesday moved from the BWI airport last Friday afternoon to a street address in an Atlanta suburb that evening. One from the coffeehouse moved from the engineering building of Ruhr-University in Bochum, Germany, across the main road to the university center. It’s unclear, however, how frequently the database is updated, and the locations for those two devices have not changed again since last week. In a statement, Google said: “We collect the publicly broadcast MAC addresses of Wi-Fi access points. If a user has enabled wireless tethering on a mobile device, that device becomes a Wi-Fi access point, so the MAC address of such an access point may also be included in the database. Wi-Fi access points that move frequently are not useful for our location database, and we take various steps to try to discard them.”
Google did not respond to a series of questions posed last week, including what measures it takes to filter out mobile devices and laptops from its database, what privacy policy governs this data collection, and whether law enforcement or civil litigants submitted requests for records from its database. The company also declined to specify how someone can remove their device’s MAC address from the database, and a question asking that in a support forum last September was never answered. Android devices appear to take one privacy-protective step that Apple iPhones do not: they randomize their MAC address when acting as hot spots, using a range of addresses that are marked as unassigned. To be sure, it’s not entirely surprising that the whereabouts of devices acting as Wi-Fi hot spots are swept up in these ambitious efforts to map the planet’s access points (which can also let desktop computers without GPS functionality learn their locations). More and more phones offer tethering, which came to the iPhone last year, and 4G hot spots are becoming more common. One way to filter out mobile MAC addresses would be to compare them against a list of manufacturers. If it’s an HTC-issued address and HTC doesn’t make fixed wireless access points, that could be discarded. Linksys devices, on the other hand, are probably more likely to remain in one place.
[ttjad keyword=”android-phone”]




![Read more about the article Web Browser Speed Test between Windows Phone 7 vs iOS 4[Video]](https://thetechjournal.com/wp-content/uploads/wp7iphone-brows-300x186.png)