Pwn2own hackers finally break into the Google Chrome sandbox with sophisticated exploit and according to the firm, the exploit relies on some newly discovered zero day vulnerabilities, works on all Windows operating systems and could give malicious websites the ability to download code from a remote source and execute it on a user’s computer……….
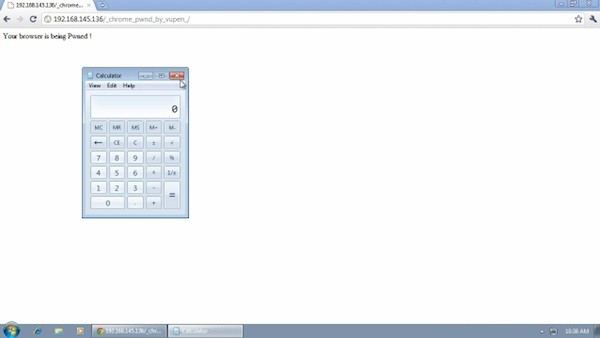
After emerging unhacked from the last three Pwn2Own hacking competitions, Google Chrome which is one of the most secure web browsers available today has finally been hacked.A French security research firm boasted that it has discovered a two-step process for defeating Google Chrome‘s sandbox, the security technology designed to protect the browser from being compromised by previously unknown security flaws. Experts say the discovery, if true, marks the first time hackers have figured out a way around the vaunted security layer, and almost certainly will encourage attackers to devise similar methods of subverting this technology in Chrome and other widely used software.VUPEN Security said: “We are (un)happy to announce that we have official Pwnd Google Chrome and its sandbox.” The post includes a video showing the exploitation of what VUPEN claims is a previously undocumented security hole in Chrome v.11.0.696.65 on Microsoft Windows 7 SP1 (x64).“While Chrome has one of the most secure sandboxes and has always survived the Pwn2Own contest during the last three years, we have now uncovered a reliable way to execute arbitrary code on any installation of Chrome despite its sandbox, ASLR and DEP,” the advisory notes. ASLR and DEP are two of the key security defenses built into Windows Vista and Windows 7.
Google spokesman Jay Nancarrow said the company was unable to verify VUPEN’s claims, because VUPEN hadn’t shared any information about their findings. “Should any modifications become necessary, users will be automatically updated to the latest version of Chrome,” Nancarrow wrote in an email to KrebsOnSecurity.Chaouki Bekar, VUPEN’s CEO and head of research, confirmed that the company had no plans to share any details about their findings with Google, nor was it aware of any steps users could take to mitigate the threat from this attack.“No, we did not alert Google as we only share our vulnerability research with our Government customers for defensive and offensive security,” Bekar wrote in response to an emailed request for comment. “Unfortunately, we are not aware of any mitigation to protect against these vulnerabilities.”Jeremiah Grossman, a Web application security expert and chief technology officer for the security consultancy WhiteHat Security, called the news “quite serious.”“We have governments competing for 0days, and we’re not even sure who the buyers are, maybe the US government didn’t get the 0day,” Grossman said “One way or the other, consumers are unprotected from an 0day we can’t really verify but probably exists. I think that’s quite serious.”
Bekar explained that the exploit they devised uses two distinct vulnerabilities: The first one results in a memory corruption and disclosure leading to the bypass of ASLR/DEP and execution of the first payload as low integrity level (inside the sandbox). A second payload is then used to exploit another vulnerability which allows the bypass of the sandbox and execution of the final payload with Medium integrity level (outside the sandbox).Grossman said that even if VUPEN’s claims can be proven correct, he would still consider Chrome more secure by default than either Firefox or Internet Explorer. “As VUPEN’s research indicates, to exploit Chrome you have to have two vulnerabilities, not just one. With Firefox and IE, you just need one vulnerability in those browsers to compromise the machine.” Also, he said, Chrome applies security updates automatically, and aut0-patches third-party plug-ins like Flash, often days before Adobe releases the stand-alone patch for Flash.It seems odd that VUPEN would brag about a flaw that it plans to sell to government clients for offensive purposes, since doing so might tip off potential targets to be extra cautious. This also raises the question of how long it will be before hackers figure out a way to defeat the sandbox technology surrounding Adobe’s Reader X, which the company said was based in part on Google’s research. Currently, there are several zero-day vulnerabilities that Adobe has put off patching in Reader X, out of an abundance of confidence in the ability of its sandbox technology to thwart these attacks.
[ttjad keyword=”general”]




Dandy, but can you read/write outside a WP7 sandbox?
Dandy, but can you read/write outside a WP7 sandbox?